Most modern cyber-attacks follow a unique pattern – a pattern that repeats itself over and over in every case. It starts with a recon exercise during which an attacker scopes out the exploitable soft spots in the network from the outside. Using one such vulnerability, they get in, arm themselves, transfer the payload, and slowly but surely compromise the target. The key to neutralize an attack? Disrupt the kill chain as early as possible. But what is infinitely less messy and less costly is to block the attack before the sequence starts to form.
At the recent Security Field Day event in Silicon Valley, Fortinet presented FortiRecon, a recently released solution that is designed to help organizations obstruct threat actors at the pre-attack stage, and in case they’re already inside, break the attack sequence early in the cycle.
Mixed Blessing
The network is elastically expanding in all directions, so more things can fit in – more assets, more data, more users. But at the same time, the relentless expansion has caused the boundaries to dissolve and the perimeter to blur. Populated with a growing list of public-facing assets, and with an undefended perimeter, the attack surface is supremely complicated, and exceedingly hard to manage or secure. So, how do we put the genie back in the bottle?
One way to secure the perimeter would be to understand the kill chain – follow the breadcrumbs, identify the moving parts and nip it in the bud before it wreaks network-wide havoc.
Organizations have spent insane amounts of time and money forensically reverse-engineering cyber-attacks to trace the steps and understand the methods of attackers. But that is after the attack has been orchestrated and damages have been sustained. Another way is to review the organizational risk profile from time to time and do what it takes to reduce the risk itself so that the network doesn’t have wide open blind spots for attackers to sneak through.
A Vision Ahead of Its Time
Operating at the intersection of network and security, Fortinet has a sophisticated understanding of the current-day threat landscape. Through years of research and engineering, Fortinet immersed itself in dissecting the anatomy of cyberattacks. And now in the wake of growing cyber breaches, Fortinet puts its learning to work to design practical and intelligent solutions that can block an attack.
Built over the two decades that Fortinet’s been in business, its portfolio is a sprawling list of products and solutions. Its ever-evolving security products deliver a solid defense to any digital environment. Fortinet enjoys patronage of customers around the world and to this day, has shipped out over 9 million firewalls.
The founders of Fortinet saw the fields of network and security converging long before it happened. So, they focused on building security solutions that fortify the the network as it grows and changes.
“Our vision for the company is to be able to put all of these products together into what we term as security fabric, and security fabric to us is a way to make all our products interoperate,” says Carl Windsor, SVP Product Technology & Solutions.
With that objective in sight, Fortinet brought to life a range of technologies whose primary mission is to make sure that the network does not look like an open invitation to nefarious actors. Under the hood, Fortinet has a product for each stage of the kill chain that can potentially check the infection in its tracks.
All of Fortinet’s security products revolve around FortiGuard Threat Intelligence, the information core of the Fortinet Security Fabric. Fortinet’s team of researchers incessantly feed this system with information on the latest strains of threats and vulnerabilities. The Threat Intelligence shares this information across the board, updating the products and solutions in its orbit with the latest intelligence.
Fortinet’s Latest DRP Offering – FortiRecon
At the recent Security Field Day event, Fortinet showcased FortiRecon which was announced June of this year. At the presentation, Carl Windsor gave a high-level overview of the cyber kill chain and demonstrated how organizations can detect, prevent and respond to attacks using FortiRecon.
“The idea behind FortiRecon is to give customers and users the ability to see what threat actors are seeing about their organizations.” Simply put, FortiRecon lets you step into the shoes of an attacker and view the open doors in your network through their lens.
According to Windsor, FortiRecon’s “early intelligence” or “early warnings” can help organizations dynamically locate the weak points that entities outside the perimeter can see when looking at the network.
FortiRecon helps tackle an attack in two ways – by helping to “understand the organizations’ risk profile” and to respond to the attack swiftly.
FortiRecon is a Digital Risk Protection (DRP) service, the only solution out there to perform the three functions of External Attack Surface Management, Brand Protection and Adversary Centric Intelligence.
Windsor clarifies that FortiRecon is not a vulnerability assessment tool, but a monitoring solution whose function is to discover new devices, check for security issues and identify changes. It automatically discovers sundry network assets including cloud resources and devices. Upon discovery, FortiRecon scans each asset for security issues like vulnerabilities, exposed services and misconfigurations.
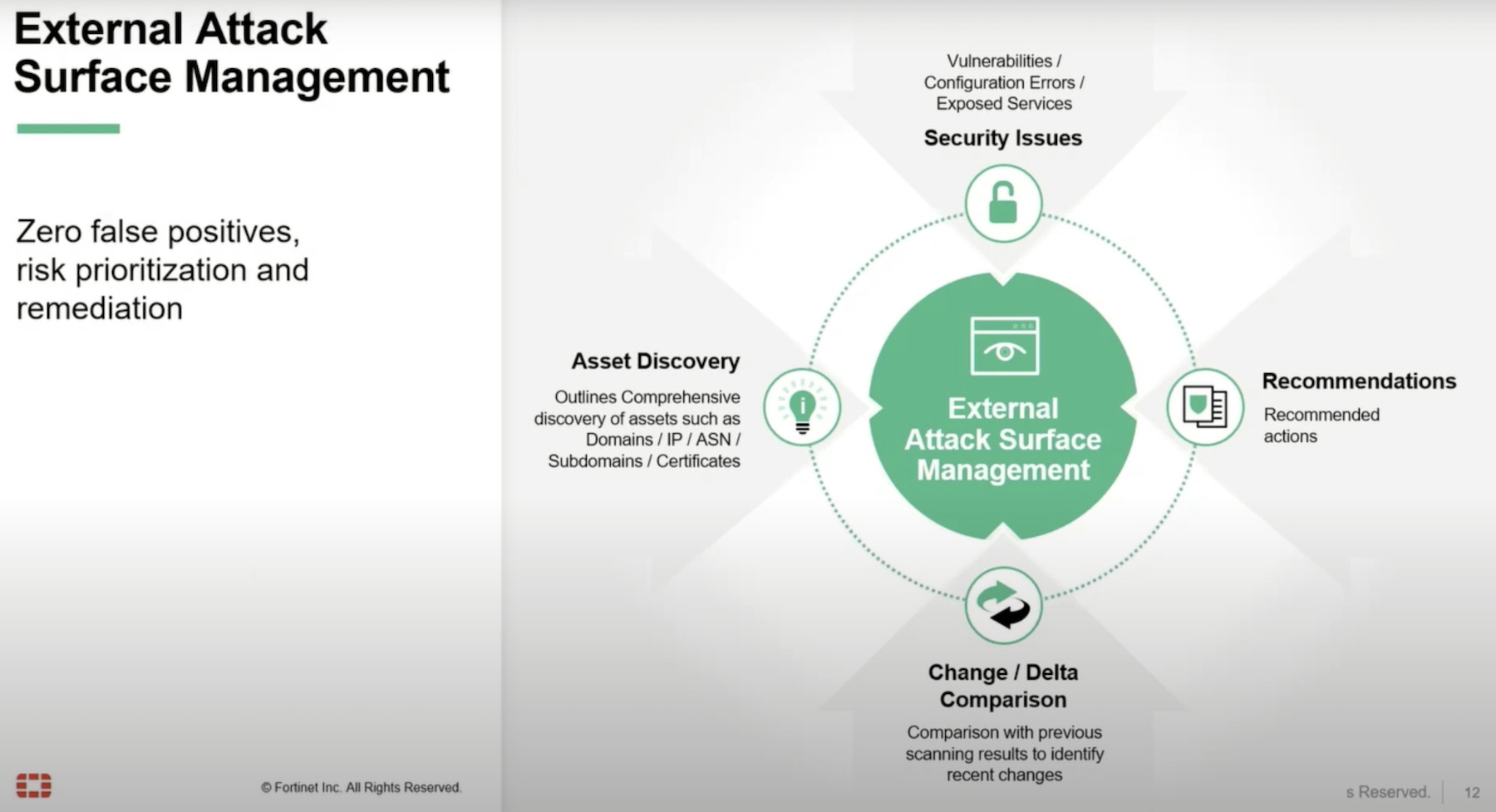
Windsor explained that FortiRecon identifies every vulnerability on the external attack surface that can be viewed by a third party. This includes the big holes like ransomware, configuration errors, unprotected secrets and assets, leaked credentials, but also smaller chinks like fake social media accounts and suspicious mobile apps.
Based on the findings, it curates recommendations and sends them out to the administrators. But instead of blindly firing alerts , FortiRecon intelligently prioritizes them according to risk level before dispatching them so that administrators have a hierarchy to follow.
FortiRecon also provides protection going outside the immediate attack surface. The Brand Protection component covers a wide range of activities pertaining to brands that are happening out on the Internet. It monitors leaked credentials, typosquatting, rogue applications, social media discussions and phishing campaigns. The endgoal of including brand protection in the capabilities of a monitoring solution is to preserve customer loyalty and brand image.
The last piece that Windsor sheds light on is the Adversary Centric Intelligence which is intelligence coalesced from all over the attack surface and formatted to be digestible and actionable.
Wrapping Up
The network with its exploding amount of assets and technologies presents tremendous opportunities for threat actors. Armed with sophisticated weapons and the right tactics, any nefarious actor can sneak in through a blind spot and abuse the system. In this reality, FortiRecon is an indispensable item to have in the security tool kit. It not only makes it possible to block a breach or tightly check its impacts through early detection, but it really addresses the core issue of understanding the organizational risk profile. The custom intel it provides is critical to gauzing the risks and doing away with the vulnerabilities that reveal themselves to an attacker at an pre-attack stage, and finally improving cyber hygiene.
To see FortiRecon in action, watch the demo at the end of the presentation. Watch Fortinet’s other presentations from November’s Security Field Day event for demos of more recently released security products from the house of Fortinet.