Last month, HashiCorp’s Boundary Enterprise launched into general availability. A self-managed access management solution, Boundary Enterprise enables companies in highly regulated industries that cannot use public cloud or SaaS, secure remote user access to private resources in their environment.
But before going into what the new offer has in store for enterprise users, let’s have a little context first.
Organizations’ transition to cloud may well be over, but their security journey is far from complete. Reports of malicious entities breaking into private networks and taking control of assets make headlines every day.
This has pushed CISOs towards driving identity-based security awareness within their organizations. Identity-driven security addresses a myriad of past and current security challenges faced by organizations.
Identities and Accesses
Every day, upwards of million identities – namely human users and machines – connect to private resources residing inside corporate networks. These are people working for the organizations, as well as external entities like vendors, contractors and so on. Their levels of access are as dynamic as the data and services they connect to are ephemeral.
These vagaries, coupled with the emerging risks associated with the flex work model, have created massive security holes in the form of access vulnerabilities in a borderless network that has no clear beginning or ending point.
In security, there is a long-held article of faith that the perimeter is the primary point of security. Now as the familiar margins have started to blur, this theory is put to question. At the recent Security Field Day event in Silicon Valley, while demoing the new Boundary Enterprise, Pete Pacent, Boundary Product Lead, HashiCorp emphasized on this.
“As organizations adopt cloud, not just as a specific location of deploying resources, but rather as a paradigm of doing things, networks become more logical in nature as there’s no longer a physical concept of the network. Security too becomes more of a logical construct where you have to secure runtimes and people across different unknown spaces. So, as organizations adopt multiple different cloud providers, as the concept of network becomes more logical in nature, the emphasis of security shifts from the actual network perimeter to the concept of identity as your source of truth,” says Pacent.
Protecting a Borderless Perimeter
The segue to this new kind of network powered by modern infrastructures has organically driven organizations to a zero-trust security model, giving way to a crop of new access management solutions to emerge.
Zero-trust security advocates for giving identity absolute priority. For this model of security, it all comes down to how identities are authenticated and how they’re accessing the infrastructure.
HashiCorp embraces this new security philosophy for all its products. “Some of the transitions that we’re seeing in the security industry over the last few years really underpins how we think about security at HashiCorp,” says Pacent.
HashiCorp’s secure remote access offering, Boundary offers a way to standardize remote user access to cloud infrastructure. The product, which is HashiCorp’s one of most iconic offerings, enables enterprises to manage and secure access across users, applications, devices and data.
Setting Boundaries with HashiCorp
Boundary works by creating a consistent access workflow that gives users the least privilege access controls across a diversity of endpoints. The principle of least privilege (PLoP) gives users and entities access to only essential resources that are required to complete a given task.
With Boundary as the proxy between identities and target hosts and services, organizations can leverage automatic authentication and authorization of every user requesting access, whether they are an insider, or outsider.
This rigorous vetting creates “very granular authorizations that allow users to connect to whatever infrastructure systems they might need to connect to, on whatever cloud provider or location they might be on,” says Pacent.
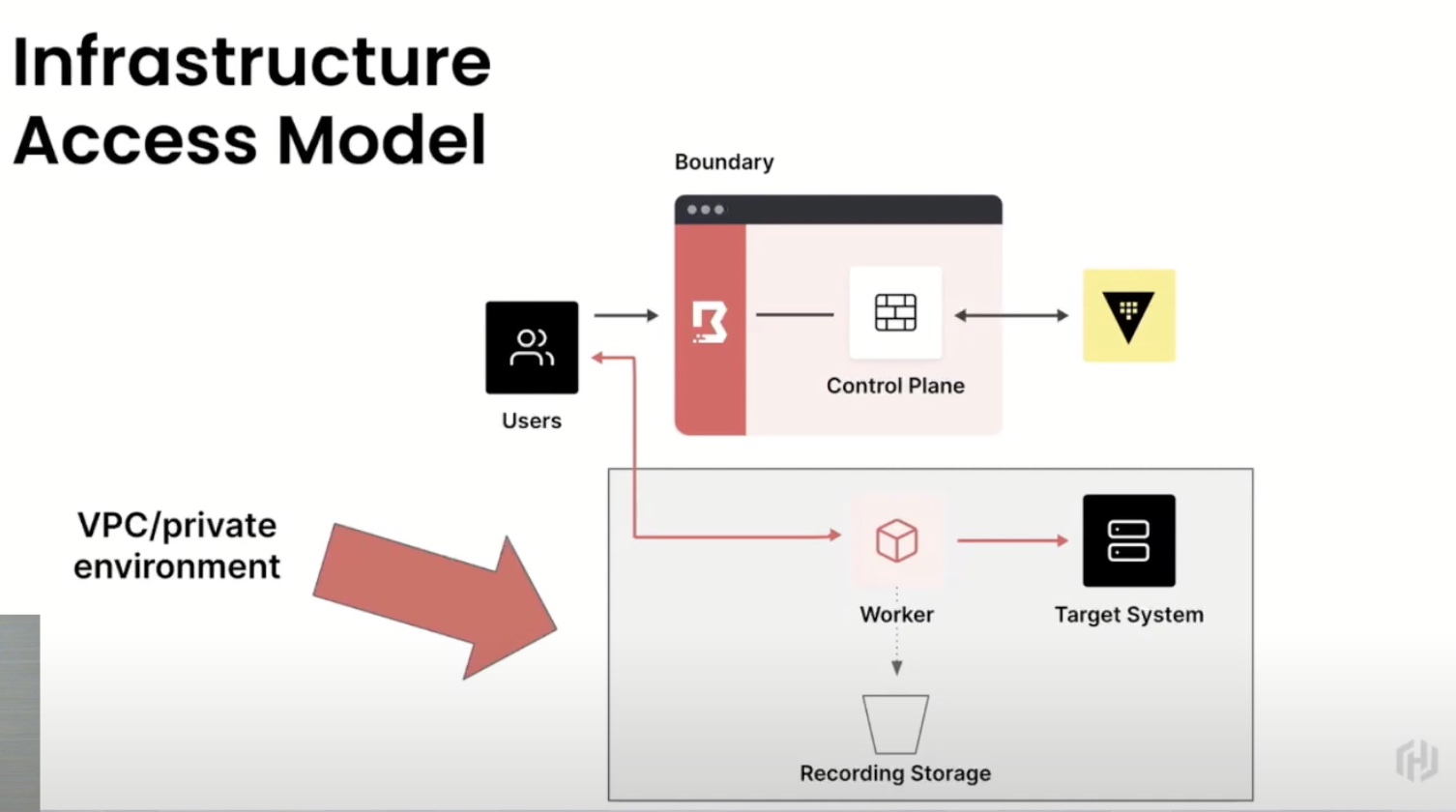
The access model fortifies the network further by ensuring that across endpoints and end users, clients don’t have standing access. A new credential is generated dynamically for every session that is either single-use, or time-based and short-lived.
Architecturally, HashiCorp Boundary constitutes two primary components – a control plane that manages the states of all targets and users and their access permissions, and worker nodes that serve as gateways through which connection is facilitated. When a session is initiated, the authenticated part of the tunnel extends from the node to the target, giving users direct access while limiting the possibilities of straying from the course. Boundary lets users record every session for deeper visibility into the transactions, and the actions and commands conducted.
On HashiCorp Cloud, the control plane is managed by HashiCorp on behalf of the clients, although they are at liberty to run the nodes in their private environments.
When measured against other access management solutions, Pacent highlights that Boundary has several advantages. A key point of difference is that it is an agentless proxy, meaning there is no need to install Boundary on target hosts and services. This is especially useful when legacy systems are involved.
“As the world shifts away from instance-based access to more API-as-the-point-of-access, we don’t really have a concept of an agent. This model is durable both for those more legacy systems as well as the modern agentless end points,” says Pacent.
It frees users from the additional hassles of deploying another component in the environment and running the overheads throughout its lifecycle.
Same Feature Set across Two Editions
Boundary comes in two flavors – a free, open-source version and the paid enterprise edition. More features and support are offered with the enterprise edition. While it is self-managed, there is also a fully managed version of Boundary that is delivered on HashiCorp Cloud.
Pacent informs that irrespective of the management models, both the offers are technologically identical. He maintains that choosing one over the other should not be dependent on the feature set or the pricing, but on whether the enterprise wants to have a fully-managed lifecycle operations or run it autonomously within their own environment. The self-managed version, more specifically, caters to organizations that are constrained by regulatory overheads to keep data within a certain region.
As of today, the self-managed version is only available within AWS US-East 1 region, but expanding it to other regions is in the near roadmap.
Wrapping Up
Identity-centric security is a core essential in the current threat landscape. HashiCorp Boundary Enterprise provides a way to sharpen organizations’ identity metrics, allowing them to standardize a least privileged access model that dynamically authenticates, grants and revokes accesses with the end goal of protecting identities within and without organizations, and the data and resources living in the network. In a time when organizations cannot afford to give in to the temptation of skipping past access security, Boundary offers a simplified way to embrace zero-trust security that covers all connection points and entities.
For a deep dive of HashiCorp Boundary Enterprise, be sure to watch the presentation from last weeks’ Security Field Day event.