The mass shift to cloud has brought with it some heavyweight challenges at the top of which is security. Research indicates that a significant majority of security breaches happening in the cloud are results of leaked secrets. So how can we better manage the secrets in our ecosystem? The answer, once again, is zero-trust security.
At the recent Security Field Day event, HashiCorp presented a couple of their zero-trust security solutions that leverage identity-based security to protect sets of sensitive information from becoming targets of insidious attackers. Among the solutions HashiCorp presented was Vault – a comprehensive secrets manager whose primary function is to encrypt and deliver secrets safely to machines and services.
Poor Habits
Modern digital enterprises own a rich diversity of assets running in disparate environments. These distributed resources have one thing in common. They all contain sensitive data, and therefore are under some kind of lock and key. Access to these assets is guarded by certain forms of privileged credentials, aka secrets, that give humans and machines permission to access.
The prolific number of assets and the fast-evolving strains of threats have made it imperative that different types of secrets are used in varying contexts to ensure high levels of security. As a result, any digital authentication credential is a secret, examples – usernames and passwords, tokens and certificates.
High-tech environments are teeming with these secrets and the current attitude around secrets management is negligent. When secrets start to sprawl, they wind up everywhere unencrypted. And without visibility or auditability, they are vulnerable, and therefore portals to the inside. And just like that, what was designed to be the lifeblood of modern infrastructures becomes the cudgel.
Taking Control
First things first, companies need strong secrets policies and best practices to keep the sprawl under control. So that from being peace of mind, secrets do not become a source of stress, every last one of them needs to be tacked down and stored in a safe location. The policies should put a stop to sharing secrets between employees and storing them anywhere but the store.
But implementing a consistent policy across the board is not an easy thing. In a situation where every application, every infrastructure has its own cyber model, what companies need is a centralized way to manage secrets, intelligently and automatically, which is more than any policy can achieve.
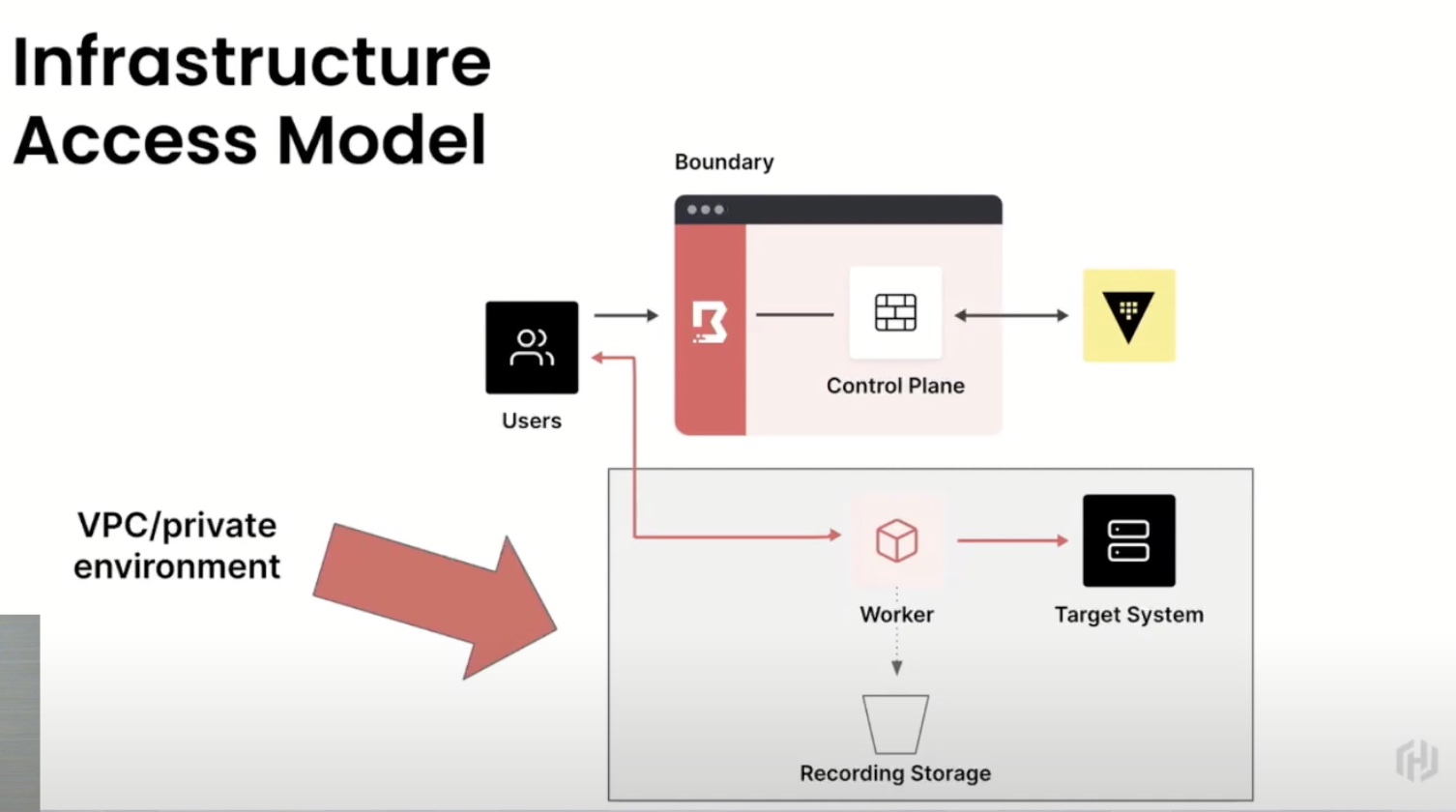
As noted earlier, Vault by HashiCorp is a secrets management platform that serves as a safe store for secrets and sensitive credentials. At its foundation, Vault has HashiCorp’s zero-trust policy of authentication and authorization. With a surprisingly simple architecture, HashiCorp has managed to fashion an intelligent solution with Vault. Rather than leaving it to employees to manage their secrets, Vault manages their secrets for them.
Nicknamed “identity broker”, presenter Rob Barnes explains that Vault “brokers identity on behalf of your target platforms, be it cloud or a database.” More on that ahead.
The big difference is that Vault is a complete solution that eliminates the need for other similar solutions. It offers encryption as-a-service that people use separate cryptographic solutions for, to manage keys and credentials. So when using Vault, those types of solutions can be averted.
Vault by HashiCorp
Barnes, Sr Developer Advocate at HashiCorp gave a deep-dive presentation of Vault at the recent Security Field Day event. He kicked off the session by talking about the key functions. Later in the session, he gave a demo of the solution.
In Barnes’ words, “Vault is a number of different things depending on how you use it.”
Vault operates in two stages- authentication and secrets generation. Authentication on Vault happens via “Auth Methods”. Users can control how they want to authenticate their applications to Vault by picking from the long list of Auth Methods available in Vault.
“You can configure any of the supported options, so that instead of storing the identities on Vault itself, you can keep them managed in that central place, ie., your identity provider, and we can log into those servers and verify the identities of people or machines that are trying to authenticate,” explained Barnes.
In the second stage, Vault generates the credentials. This is the function of a secret engine, and Vault has multiple flavors to support different cloud platforms and databases.
Barnes summed up the process with a simplistic diagram which showed how the action happens. In the first step, applications are authenticated to Vault via the chosen authentication methods. In the next step, Vault brokers a username and password on behalf of the target platform, cloud or database, for its profile API. Vault then returns this credential to the API.
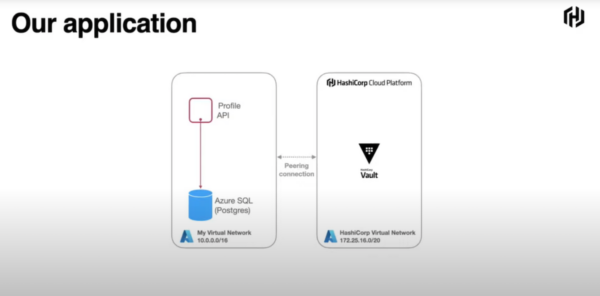
Every credential created has a lifecycle, at the end of which it is wiped out. This ensures that there are not an unmanageable number of secrets in the environment, and that they are not reused by any chance. Administrators can set the credentials’ TTL (Time to Live) from a few minutes up to several days.
While Vault requires returning applications to authenticate at the gate each time, it lends users the flexibility to use the Vault agent which offers a quicker access. Using the Vault agent to authenticate once, they can save the credentials generated in a safe location of their choosing, so that each time the application needs to be connected, it can be automatically authenticated in a quick and reliable fashion.
Vault is currently set up on the HashiCorp Cloud Platform where it is delivered as a fully managed service. The only thing customers are responsible for is the early configuration and administration based on the internal access management protocols.
Wrapping Up
Management of secrets shouldn’t fall entirely on the employees. A big part of it is the company’s responsibility. HashiCorp’s Vault shows how something that is so seemingly complex and tedious can also be done in a smart and easy way. It serves the twin purpose of dynamically generating and safely storing secrets, whilst managing them automatically, relieving users of the burden. Companies should deploy Vault in their ecosystems to not only protect infrastructure secrets but also to ensure an overall improved security culture inside the organization.
For more information on Vault, check out the second part of the presentation and other demos by HashiCorp from the recent Security Field Day event.