In today’s network security landscape, one may act on the information they have at hand, only to find that said information was misleading or didn’t paint the full picture of what’s really going on in the network. In the face of these mysteries, Kemp and their Flowmon product displayed at March’s Security Field Day event hopes to collect all of the pieces of the security puzzle in one place so that IT teams are armed with the right information to guide their security decision making.
Puzzles vs Mysteries, and the Security Space
If you’re into security like I am, then chances are you probably are equally interested in the world of puzzles and mysteries. The critical thinking mindset required to excel at puzzles and mysteries is the same one that many security professionals operate in on a daily basis. An interesting question (or puzzle perhaps) to ponder is this: what is the difference between a puzzle and a mystery?
Many blogs have already tackled this topic, so I would just like to share the consensus and how it relates to security. Paraphrasing national-security expert Gregory Treverton who is cited in Malcolm Gladwell’s New Yorker article, a puzzle is a problem that can be solved through one or two simple, factual answers, key bits of information that ultimately uncover the desired result. A mystery, on the other hand, has lots of information involved, some of it is misinformation, meaning that even if someone gathers a silo of potential clues, only some of them are actually relevant, and others, in fact, may be intentionally misleading, or red herrings if you will.
From the perspective of a security professional, the difference between the two is something like this. A puzzle from a security standpoint would be, say, a single machine infected with malware. After finding out that the user clicked on a phishy email, opened a link, and downloaded a .exe file, then you might be pretty sure that the puzzle of the malware is solved.
Alternatively, your entire fleet may be infected with malware, and armed with the same info about said user clicking said phishing email, you might assume that they downloaded the malware, and then it spread to the others over time over your network. Without more information and a way to sift out the good info from the bad info, you may just stop there. In reality, however, the truth may be that the user in question is actually an insider, who downloaded the malware so they could put it directly onto your infrastructure, which then leached out to the fleet. The actual answer here is a mystery, as you wouldn’t have a full picture without acquiring all the information and parsing out the truth from the misinformation.
Addressing Security Mysteries and Puzzles
This problem of mysteries in the realm of security is exactly one that Kemp intends to solve. Although known for their application load-balancing capabilities, Kemp also leverages that integration with the network to provide visibility into app-related network actions through network detection and response (NDR) with their Flowmon product.
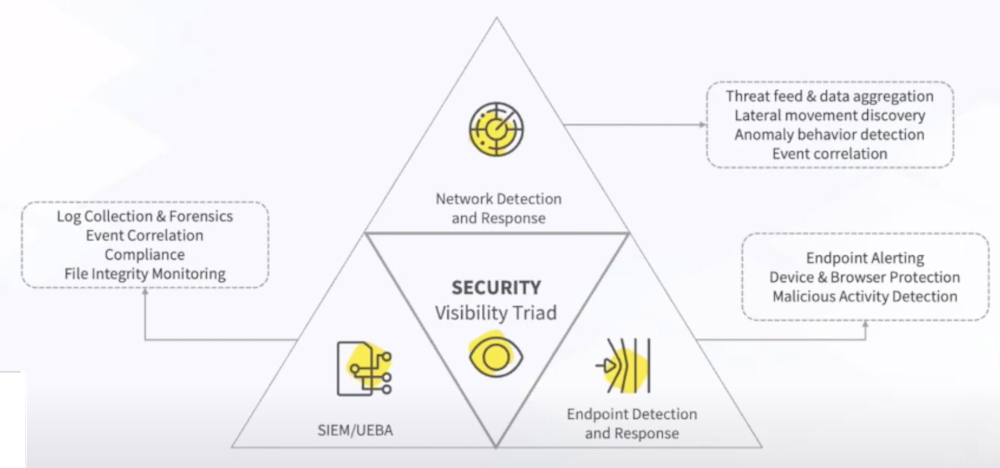
As shown in the security visibility triad above, NDR is a crucial part of identifying potential threats and attacks to the network, and doing so as early and often as possible. Kemp’s Flowmon does this by providing high-level visibility into network activities, using machine learning to filter through all of the individual data points generated by your organization, and hone in on the information that actually matters.
Solving Mysteries with Flowmon
In their appearance at Security Field Day in March, Kemp’s VP of Product Strategy, Jason Dover, described the capabilities of Flowmon and how they relate to uncovering the mysteries of modern security threats.
Dover uses the term “threat intelligence,” digging into the insights gained through NDR via Flowmon. By ingesting data from around the network and analyzing it through ML, Flowmon helps security professionals to hone in on the data that matters most, filtering out the noise of potentially misleading data points.
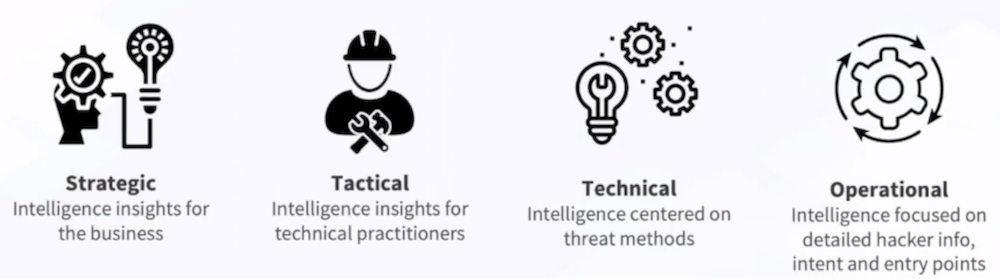
In each of the four areas above, Flowmon builds a clearer picture of the state of the network, making it more obvious when something is awry. Although by no means is this a silver bullet, Dover and the rest of the Kemp team believe that Flowmon is a key facet in helping security teams turn their mysteries into more solvable puzzles.
Zach’s Reaction
Kemp’s Flowmon helps IT organizations identify the right information regarding security threats in their network, making it easier for them to address issues quickly and regularly. As far as puzzles go, it seems like the answer to the puzzle of gaining visibility over your network is Flowmon.
To learn more, watch the rest of Kemp’s Security Field Day presentation, tune into their recent appearance at Networking Field Day, or simply visit their site for other resources and technical documentation.