Security is critical to any network, especially when it involves Zero-Touch Provisioning. ZTP comprises a lot of access devices and connections all of which could very easily go kaput if vulnerabilities are not dealt with ahead of time. That’s why secure device onboarding is a must to maintain a fully secure network. Cisco brings to offer an implementation on its IOS XR which it showcased in the Networking Field Day: Service Provider event in December whose function it is to bolster security in ZTP workflows.
Security Concerns with ZTP Workflow
The primary reason why security remains a priority with ZTP workflow is because access devices are commonly in insecure locations and that makes the entire network vulnerable to threats. Different vendors’ implementations of ZTP have a lot in common but are also different in some very pivotal ways, starting with the options that are sent out from the device to the DHCP server and the ones you get back. Many a time, it falls on the operator to get around an abstraction and figure out a way to keep things working in a consistent fashion.

What most businesses seem to want with respect to this is a system that supports ZTP workflows without the users having to depend solely on vendor-specific options. The systems that we see today support automation from day zero but are often not secure in the ways one would imagine. There is no way for the device to trust the network nor the network to trust the device.
Cisco, a Frontrunner for Leading Technologies
Cisco needs no introduction in the tech space. An American technology conglomerate with headquarters in California and footprints all over the world, Cisco’s contribution to the development of Silicon Valley is general knowledge to America.
In business for several decades, Cisco has an expansive portfolio featuring a bunch of software, hardware and telecom equipment in addition to other products and services. It’s specialties in recent times are IoT and energy management.
Inside Cisco’s Secure Zero-Touch Implementation
During the Networking Field Day: Service Provider presentation, Cisco’s TME Tech Lead, Akshat Sharma gave a presentation of Cisco’s implementation of secure Zero-Touch on its IOS-XR. He later offered a deep-dive into the details of the implementation and explained how through it seamless trust is enabled from day 0.
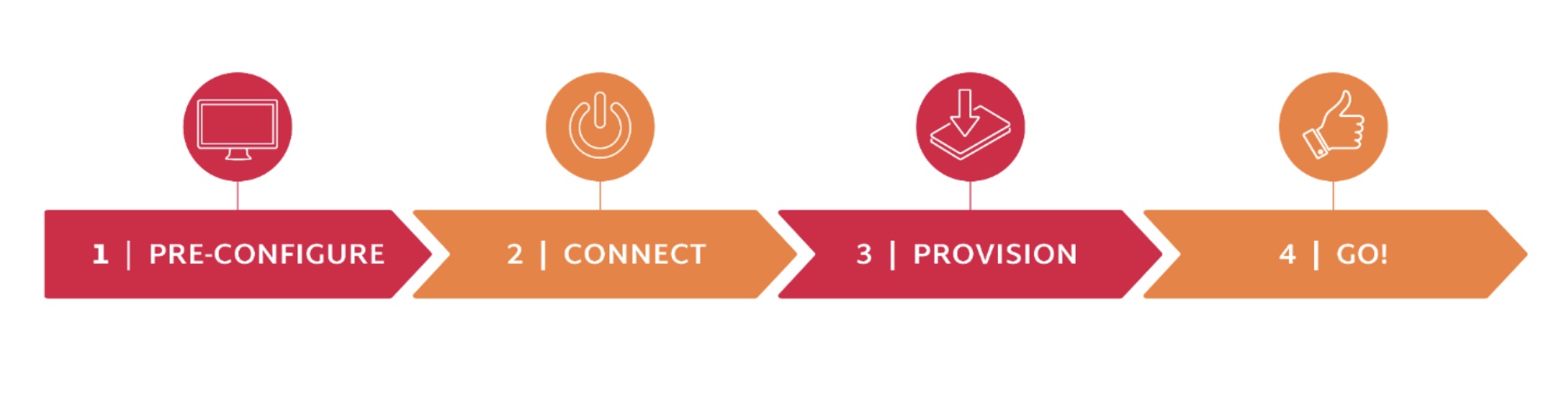
Cisco’s goal with this feature is to offer end-to-end security as required to keep the zero-touch workflow going. The idea here is to avert the one-touch workflow where devices are first taken to a pre-staging facility and then again transferred to the installation site.
In this implementation, Cisco addresses the security considerations of ZTP workflow which often get neglected in the rush to achieve seamless automation. Cisco secures ZTP in three fashions, namely, through router/client validation which happens at the time when the router joins the network, network/server validation which happens when a router without any configuration has to validate and accept a network and artifact validation which is validation of config, script or any artifact that is downloaded from the ZTP server.
These it accomplishes through the Cisco TAm, Unique Hardware Identity SUDI and Owner Certificates. The TAm chip is anti-theft and anti-tamper in design, has built-in crypto functions and offers secure storage. RFC-8572 compliant, this implementation enables the hardware root of trust to keep ZTP secure end to end.
The Verdict
All said and done, Cisco’s implementation seems promising to the goal of securing ZTP in a way that enterprises today need to ensure end-to-end network security. When compared with the products of other secure ZTP vendors, it appears that Cisco’s implementation has tied many of the loose ends making ZTP security more airtight.
Check out Cisco’s presentations at the Networking Field Day: Service Provider to learn about the implementation in full details. To know more about their products and services, visit Cisco’s website.