The answer to our old security problems was easy. All we need to do is install an agent and get devices on a VPN and the problem is solved! That’s the old way of securing things in a nutshell. The issue is that new devices aren’t quite so easy to modify.
The primary form of communication that most of the world uses now is more mobile than ever before. The world of desktop computers wired to the corporate network with a customized software load is gone. Instead, we have mobile phones being used as the primary interaction device running software that has been hardened and applications that must be approved in a walled garden in order to even function. There is no room to insert any agents or controls for our security teams to monitor and configure. It would seem that our users are roaming around the Wild West of devices with no order to what is going on.
5G Is The Frontier
As we move toward the new mobile protocol paradigm of 5G, opportunities to create order from the chaos of client devices are available. One of those ways comes courtesy of the way that mobile operators are standardizing on technologies in order to ensure maximum compatibility. With the way that 4G/LTE was built out, providers would introduce technology and then race to have it adopted as a de facto standard by others. That type of innovation doesn’t scale any longer. With 5G, providers are working together to make it easier to manage and operate networks. And their work is a boon to those trying to integrate solutions into the 5G networking stack.
One of the companies that is doing a lot of work in this space is Exium. I recently had the chance to sit down and talk to Farooq Khan to learn a bit more about what they’re up to and how it could change the way we look at protecting mobile endpoints. Current thinking around security for mobile endpoints relies heavily on things like legacy VPN connections and user-based device controls. These are sub-optimal and often invasive to the end users that just want to get their device connected and consuming cloud resources.
Exium takes a different approach. They’re working to integrate directly into the 5G networking stack on the device instead of using VPN tunnels or invasive agents. With that kind of access they can offer a Software-as-a-Service security platform to enable safe and secure computing from user endpoints. This kind of stack integration means that they can push traffic to their Intelligent Cybersecurity Mesh to ensure user data is secure and requests are valid. Transmissions are encrypted and access is verified with cloud tools.
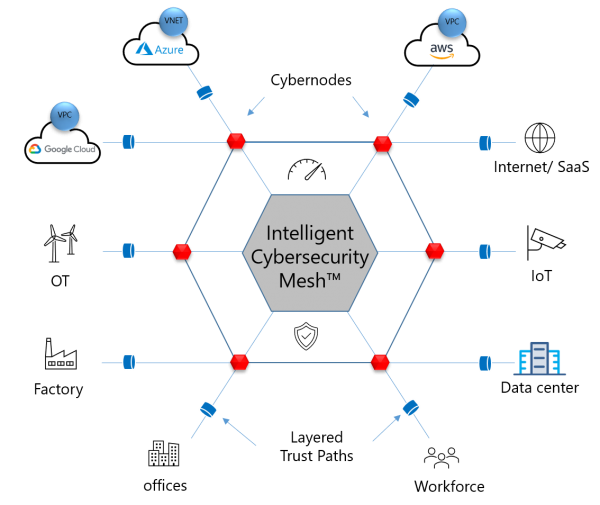
If you are saying to yourself, “This sounds an awful lot like SASE” you’re not wrong. Secure Access Services Edge is a new shift in the way we think about remote branch office connectivity. The only thing missing in the SASE model is what happens when the branch office becomes a Work From Anywhere situation with hundreds or thousands of remote workers instead of dozens of branch offices. Exium is building out a solution that works per-device, not just per-office or per-connection.
As we move forward into the world of a remote workforce on hardened mobile devices, we need to disabuse ourselves of the separation of networking and security being separate entities. We’re already working in the enterprise to combine these teams together to create operational teams that work together to ensure proper availability of resources no matter where they are or who may be accessing them. As time moves on and the way our users interact with their applications and their services changes it will be the novel solutions like stack integration that help us continue to give them the safety and security they need.
Bringing It All Together
Exium is doing a wonderful job of solving a critical security problem in a unique way. The world is moving to cloud resources accessed from a diversity of devices. We can’t keep relying on the same solutions to secure things and hope that they do a job good enough to keep people out of places they aren’t supposed to be. Instead, by offering up ideas like integrating with the 5G stack on mobile devices and building a mesh network of secured connectivity that enhances user productivity securely, Exium is going to help users go to the places they need to be in the future, whether working from home or the office or anywhere in between.
For more information about Exium and their Intelligent Cybersecurity Mesh, make sure to check out their website at http://Exium.net