Implementing a zero-trust approach to network security simplifies the process of securing remote workers, but comes with a steep technical climb to actually roll out at scale. We had the exciting opportunity to chat with Safe-T about how their ZoneZero product simplifies the implementation of zero trust, both on-prem and in the cloud.
Rolling Out Zero Trust Across a Decentralized IT Environment
Zero-trust network access (ZTNA) is all the rage in the IT security scene, especially nowadays with employees working from everywhere in this decentralized era of IT. Unfortunately, for many, the very decentralized nature of IT that zero trust is so apt to protect also introduces difficulties, especially as employees need access to resources both in the cloud and on-premises.
Many IT departments rely on VPN infrastructure to securely connect users back to on-prem resources in attempts to build a zero-trust security approach. Although effective for creating secure connections, VPNs can’t be used to control access to cloud-based resources, and generally require extensive technical chops to set up correctly and at scale. Additionally, VPNs are only a part of the greater whole of a zero-trust approach, meaning organizations need more to ensure they’re secured.
Implementing a Software-Defined Perimeter for Zero Trust
Safe-T provides a solution to the problem of implementing ZTNA across an environment with their ZoneZero product. Deployed on virtual machines, ZoneZero creates a software-defined perimeter around on-prem resources, working in tandem with your existing VPNs and firewalls to control access. ZoneZero is operated via an on-prem controller, which allows you to keep total control over your requisite certificates and keys, a must-have for compliance / regulatory requirements.
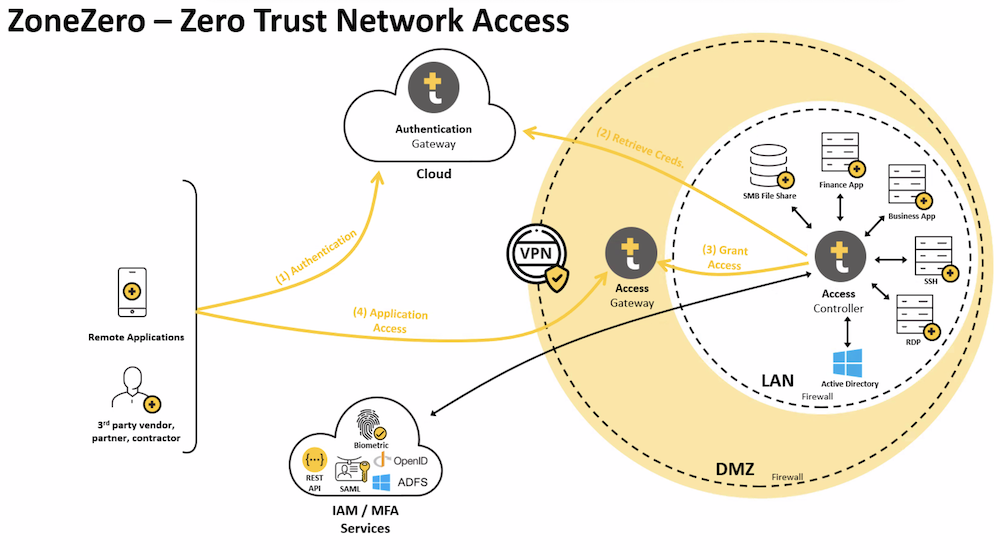
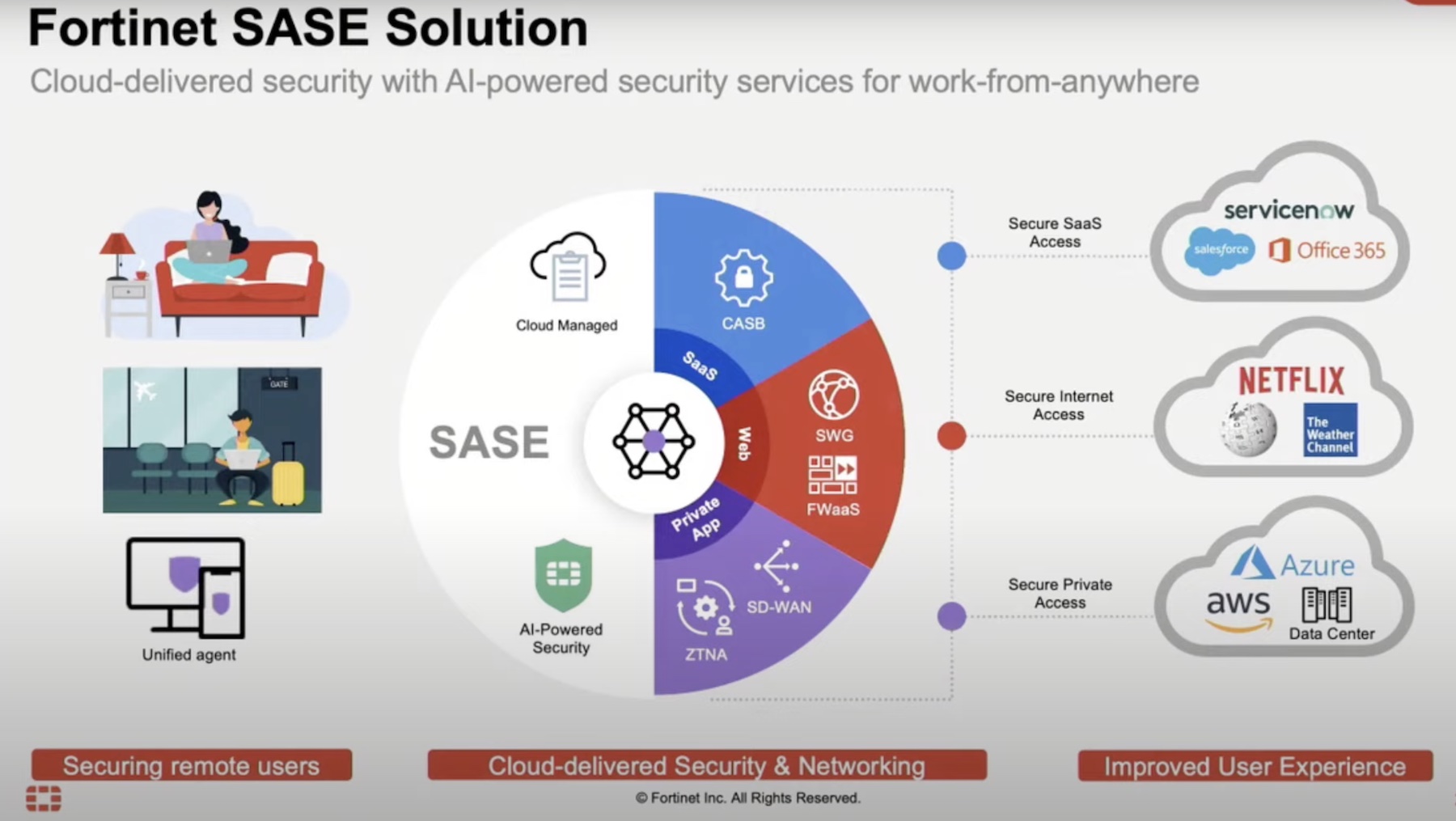
As shown in the diagram above, Safe-T integrates with your existing identity providers (IdP) — both on-prem and in the cloud — to establish an identity source of truth. Then, using authentication from those IdPs, Safe-T provides access to resources, whether through the access controller on-prem or the authentication gateway in a browser. As such, Safe-T can authorize access to all TCP-layer applications, as well as those housed on-prem — regardless of where access originates.
Going Deeper into Safe-T
We here at Gestalt IT had the express pleasure to chat with Safe-T Co-founder, Eitan Bremler, to discuss the ZoneZero product and how it can be used in a zero-trust environment. According to Bremler, a core goal behind Safe-T is to make the switch to zero trust as simple as possible for organizations. Once implemented, ZoneZero simply needs to integrate with your existing IdP, apps, infrastructure, VPNs, etc. Then, you’re well on your way towards a strong, zero-trust approach to security.
In addition, since the product works both with and without existing VPN infrastructure, organizations can and have used Safe-T to move off of their VPNs completely. That way, employees can access all of their resources securely without having to jump through the usual hoops of VPNs. On the flip side, IT admins have less to worry about, rest assured that their users are more secure without having to concern themselves with VPNs.
Zach’s Reaction
As an ardent follower of the zero-trust space, I am so excited to have learned about Safe-T and their ZoneZero product. It seems to me like one of the most simple yet highly effective ways to roll out zero trust across an entire environment.
Thanks to Eitan Bremler for sharing with us about Safe-T! For more exclusive content on the up-and-coming tech in the enterprise IT industry, be sure to read more here at GestaltIT.com.