Healthcare companies tend to have a good amount of sensitive data. Personal Health Information (PHI) and Personally Identifiable Information (PII) are the two main types of sensitive data for healthcare companies but there are other types within their systems, such as salary and other human resources information. One of the biggest challenges when dealing with sensitive data is making sure approved staff can use it while keeping it secure from those who should not be able to access it. As the head of IT Security for a healthcare services company, I can tell you that losing control of sensitive data (especially our clients’ data) can keep me up at night.

Healthcare Regulations and Compliance
Regulations add to this sensitive data dynamic. There are plenty of industry regulations, such as the Health Insurance Portability and Accountability Act (HIPAA), that force companies to enforce security measures on sensitive data. Additionally, there are governmental regulations. The first governmental regulation, General Data Protection Regulation (GDPR), came into force back in 2018, impacting the citizens of the European Union. This also impacted countries outside of the European Union, as it protected the citizens’ data no matter where the person was located. While the United States already had privacy legislation for different industries (such as HIPAA), multiple states, such as California, are now creating their own privacy laws. I expect that the US federal government will eventually make a federal law protecting all US citizens, possibly similar to GDPR. According to Gartner, 65% of the world’s population will be covered under some form of modern privacy regulation by 2023. There are many reasons why companies should keep their sensitive data secure, including laws and ethics; however, the penalties within data privacy regulations alone are enough, as the loss of sensitive data could be crippling.
Introducing Encryption to Healthcare Data
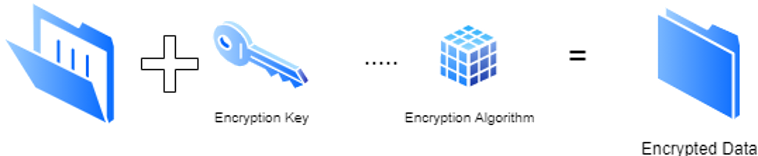
Obviously, storing sensitive data in plaintext is a recipe for disaster. Fortunately, encryption provides a solution. Encryption allows the data to be changed so that someone cannot simply access a data location and read information. Using an encryption algorithm, data is changed from being easily readable to an encoded format so that only someone who can access the private key, the variable used by the encryption algorithm to protect the data, can decrypt and read the data. To be fair, someone with plenty of time on a supercomputer could eventually crack encryption, but modern authentication algorithms would take far too many years to break. Instead of locking up all the data, organizations just need to make sure there is a secured way to access that private key. Fortunately, there are plenty of software companies that have made encrypting data much easier by automating the encryption/decryption process.
Of course, encryption is not perfect. As I stated previously, the authorized user needs to access the private key (or pair a public key with the private key in the case of asymmetric encryption) to decrypt and read the data. Therefore, anytime data needs to be modified (for instance, updating someone’s medical records) it must be turned into a usable format where it is no longer secured by encryption. The decryption process can be performed automatically by an application and then when the record is closed, the data gets encrypted again so it is saved into a non-readable format. Additionally, data can be transferred in an encrypted state from one system to another; however, the system receiving the data still needs a way to decrypt it (access to the private key) or the data remains unusable. Of course, sharing the private key is not desired as that allows for an avenue of attack. If a malicious party can get the private key, then encryption is basically useless.
Homomorphic Encryption and Intel Processors
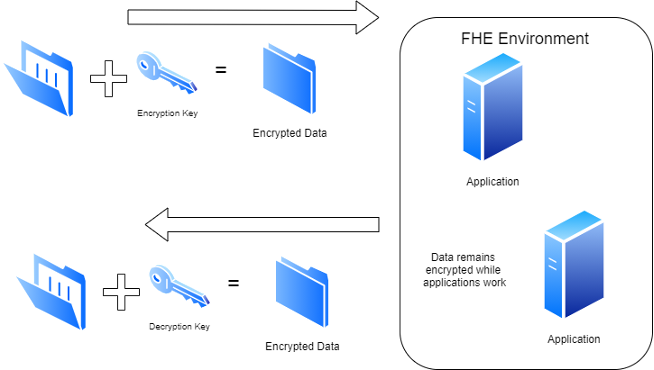
Fortunately, there is a form of encryption that can act on the data even when it is encrypted: Fully homomorphic encryption (FHE). Homomorphic encryption (HE) is different from the encryption types I mentioned previously as it allows computations to be performed directly on encrypted data without requiring access to the private key. There are three basic types of HE: Partial, Leveled, and Fully. Partial HE has existed for many years and allows either addition or multiplication (but not both) of the data without decrypting it. Leveled HE is closer to Fully HE (FHE) but it is a little more restrictive as it allows some computation on the data. However, FHE allows for generic computations on encrypted data without ever decrypting it. HE was originally envisioned back in 1978 and FHE was first constructed in 2009. You can read more about HE at https://homomorphicencryption.org. FHE has not been used in information technology partially due to a lack of standardization and software tooling; however, the major reason is that the complexity of FHE makes it very slow due to the computational horsepower needed. Processors would need to be accelerated by thousands of times to handle Fully HE workloads.
However, computational power is a strength of Intel® processors. Intel continues to introduce new instruction set architecture extensions to significantly increase the cryptographic performance of their chips. They have embarked on a multiyear program to design an application-specific integrated circuit (ASIC) accelerator for HE, the efficient operation of which has the potential to reduce the HE computational overhead. The Intel® Xeon® processors available today can perform HE workloads and the work Intel is doing for future architecture extensions will speed it up even more. Intel is delivering the processor power so software vendors can bring FHE to mainstream applications.
Bringing Homomorphic Encryption into Healthcare
Let’s take another look at the world of healthcare. Some companies generate and store lots of sensitive data. Of course, there are plenty of malicious entities that would love to get their hands on that data. The thought of a malicious party holding my company’s sensitive data hostage is enough to consider paying their ransom (note: not a recommended practice in IT security); however, if that data is encrypted then the bad guys would no longer be getting anything of value. Using the older encryption standards, the only way to work on the encrypted data is to decrypt it and that offers a time for the bad guys to obtain unencrypted data.
By using HE, data can be manipulated without decryption. This means that there are fewer times that the data is in a decrypted state, making it harder on the bad guys or even just keeping curious staff from reading sensitive data. Moving data is necessary since it does have to be shared at times, even just with another application. Using HE would mean the private key is no longer used to modify data. This is great since accessing the private key means someone can decrypt all the data, not just what is being worked on – the bad guys have less of an opportunity to get that private key. Additionally, newer techniques, like machine learning, can be implemented using FHE so organizations can extract full value from large datasets while keeping the data in an encrypted state. Keeping that data encrypted even when being changed would aid companies in keeping sensitive data from falling into the wrong hands.
Many companies, especially in healthcare, need to store sensitive data. Encrypting that data not only is a security tool but may be required by regulation depending on who the data represents or where the data is stored. By leveraging Fully HE, manipulation of sensitive data can be performed without first decrypting the data, which leaves the data in the secured format. The bad guys are getting smarter and using newer techniques, so companies must remain vigilant with the data that they must hold. It is a good thing that Intel remains at the forefront of enabling encryption technologies, including Fully HE. For more information about how Intel is enabling FHE, head on over to their site.
Intel and Xeon are trademarks of Intel Corporation or its subsidiaries.




