You’ve no doubt heard a lot recently about edge computing. With the growing power of discrete compute units like client edge devices and the recent shift in 5G technology allowing for a more standard approach to base station computing power, it’s open season on harnessing that capability. More processing is being done at the edge than ever before to save the network from additional traffic. In a digital world connecting the cloud and billions of devices also exposes it to severe disruption, data loss and inhibits business transformation.
The power and versatility of the cloud has become more important than ever because the edge has shifted to be the first stage of data analysis and aggregation before the data ever moves. Every new advance in edge processing power means more can be done closer to where the data lives.
Of course, advances in edge computing also increase the attack surface of the edge exponentially. Non-standard hardware is hard to exploit. Edge devices that aren’t smart can’t provide much in the way of a foothold for attackers. As we move toward a future where the edge is doing more of the heavy compute lifting, we also must worry about the security of those edge devices. While your first thought may immediately go to traditional security ideas like complex passwords or hardened operating systems, there is an even more important reason to make sure you have a plan for the edge.
With data receiving more attention on the edge devices, it’s important to keep in mind that errors can be introduced in the first step of the processing chain that you may not be able to detect. When the raw data is pushed back to the cloud and processed for every step there, it’s easy to spot outliers or data that can be disregarded because it doesn’t fit the pattern. Algorithms are great at making these kinds of decisions because they do not inherently trust the raw data until it has been processed.
On the other hand, if the device at the edge, whether client device or base station compute cluster, has done some processing of the data before sending it on to the next level there is an assumed level of trust. You would hope that the data aggregation and analysis software deployed there would have caught any anomalies and discarded them, right? What if an enterprising attacker were able to manipulate that data in such a way as to make it look mostly correct without arousing suspicion? On a large enough scale this could create a massive problem for distributed systems.
For example, to pre-empt the tampering of collaborative datasets, the University of Pennsylvania recently went above and beyond PHI protections while building an AI model to identify brain tumors with other research hospitals. When using the privacy-preserving method of confidential computing on their federated data sets, they protected the algorithm itself along with the data at the hardware layer with Intel Software Guard Extensions (Intel SGX).
Confidential Computing with Intel SGX
Edge to cloud security encompasses Systems, Data and Governance. Systems must be attested edge to cloud, securely onboarded, managed, be detectable and isolated if compromised. Data must be secured at rest, in transit and in use, have IP protection, data assurance and include data provenance, as well as have a way to assure privacy and confidentiality.
I sat down recently with Paul O’Neill and Ronald Perez of Intel to talk about these challenges. Paul is a big part of the confidential computing group and Ronald is an Intel Fellow now leading the many Confidential Computing initiatives across Intel, so they know what they’re doing! The talk we had was enlightening and showed me the kinds of insights, vision and lateral thinking that are needed to solve these challenges.
The key, according to Intel, is to use trusted execution environments. Intel has put a significant amount of work into their SGX initiative, and they’ve done a lot of research into how to use these secured memory enclaves in application to security issues.
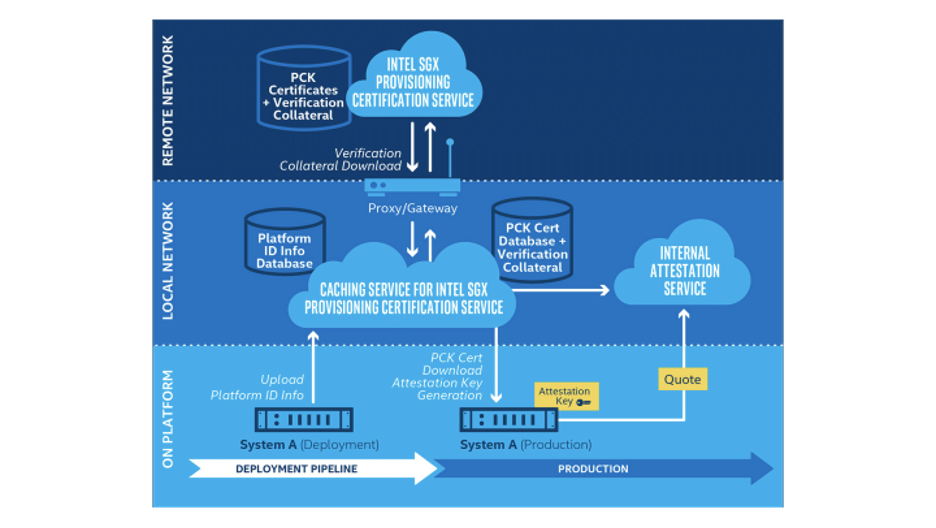
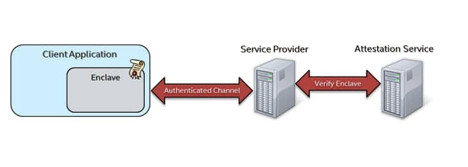
An additional layer of security comes when attestation is combined with Intel SGX to provide a method for secure communications between devices. The attestation provides confidence that both machines can exchange secrets by assuring the integrity and security of each organization’s compute environment. Data owners can have confidence that the results of data computation on SGX enabled hardware can be trusted and therefore acted upon. The more you know about what went on before the data arrived at your location the more trust you can have in the data set.
All this works if you can trust the data you’re getting from the edge. Tools like SGX ensure that you trust that data because you don’t have to worry about securing every one of those devices at all times. Because SGX can create secure memory areas to do the calculations and return the results, you can even ensure that devices are only working on things that they are cleared for. Imagine being able to classify data in levels and send out non-sensitive data to certain edge nodes while reserving the more critical calculations for nodes that you have complete confidence in. That kind of flexibility isn’t something you can get from basic ACLs or by relying on traditional security methods.
It’s a big step for a company to have complete trust in a remote data collection device, even one that they deployed. But having secured communications to that device with the ability to discover what code is running on the device and how that code was protected is a very important step in the process. It’s kind of like a bank. You would have a hard time trusting a bank that didn’t have a vault or locks on the doors, but you instantly feel better if they have a system of checks and balances and even physical security in place. You may not realize you need that assurance, but I promise you’ll notice it the next time you go in to make a deposit.
The ecosystem that Intel is building around confidential computing and SGX is going to ensure that the challenges that we face in the future won’t have to be reinvented from scratch every time something new comes along. Like the best artists, Intel has created their own tools that give them the flexibility to build anything that is needed in the future to craft a work of art. Forging a hammer is the first step for a blacksmith because that hammer is used to create everything else down the line. Likewise, Intel SGX is the first step in creating a world where data sources can be trusted and secured, and the data processing power contained therein can be leveraged to create things we can’t even dream of today.
For more information about Intel and their SGX platform, make sure you visit their website to learn more.




