Ransomware breach is an inevitable risk to entities with information technology. It has compelled users to devise innovative ways to save and secure private data, taking up their personal time. But the stress and pressure felt at the enterprise level is on a whole other level.
“Ransomware is a pressing issue that is affecting businesses worldwide. Too many organizations are crippled by it,” said Aron Brand, CTO, at CTERA – a renowned cloud storage and data protection outfit – at the recent Storage Field Day event in California.
The Fight to Recover
A ransomware attack, in any organization, has multiple implications, from big financial losses to damage to the reputation. For IT, a ransomware attack can contribute to delays in project completion, negative impacts on user experience, service disruptions, downtimes, and more. Every hour of exposure retrogrades employees’ work by weeks and months.
The post-breach period of remediation is especially a shock to all departments involved. It may divert away valuable resources from projects in progress, resulting in productivity slump.
The market is bursting with perimeter security solutions of various kinds, and it brings a sense of safety knowing that, in a time when any organization can potentially be a victim, there are techs in place to counter that. But are those solutions making security experts’ job any easier?
Brand says, “When it comes to ransomware, perimeter security only gets you so far.” He elaborates, “Perimeter security is often seen as the wall, but even the strongest walls can be undermined by a single slacking guard. One outdated machine on your network – and you often have thousands of machines on your network – that cannot run endpoint protection (EDR) is the weakest link. The attackers will find that link and they will use it to attack your NAS or your storage infrastructure.”
Exploiting these gaps, hackers have systematically breached network perimeters, often with alarming ease. It was evident that a second layer of security is required to address the situation. Thus, backup solutions came to be the last line of defense.
“A mistake people are doing is to view backup as their rescue net. The reality is that in 90% of all ransomware attacks, the backups are targeted. So once you jump, you know there’s no net there to save you. That’s the most frequent case because attackers know that if you have a backup, you won’t pay them,” he reminded.
Brand referred to a case study where a client from the manufacturing industry sustained a severe attack, to tell the audience what to expect when a ransomware attack hits out of the blue. In the said case, all of the company’s 150 edge sites went down completely, halting all operations until recovery.
“It’s very risky to rely solely on backup solutions, and particularly on solutions that don’t offer immutable storage,” he warned.
Arresting the Impact with a Ransomware-Ready Storage
CTERA believes that in the context of data breach, the two basic requirements of any storage are to be zero-trust and to provide near-instant recovery. Combined, these can minimize exposure, provide continuous protection, and unlock recovery time objectives (RTOs) measured in seconds. Although no solution provides an absolute guarantee that these requirements are met to the T, CTERA’s is the only global filesystem to have a Zero-Trust architecture.
To make sure that businesses do not derail from the baseline in any major way after a breach, CTERA offers a caching technology that provides superior recovery speed. Data is continuously replicated in the cloud. Where a legacy backup solution saves data at a cadence of 8 to 24 hours, CTERA backs up data every minute thus reducing RPO down to minutes or seconds.
In the remote storage, the authoritative copies are consolidated inside a single global file system. But CTERA knows better than to believe that just backing up data is enough. Enterprises need a storage that is resilient against the shocks of a data beach. That’s why CTERA stores all the snapshots in an immutable, air-gapped object storage environment that prevents data from being manipulated or removed, once saved.
The filesystem allows all operations to be performed using single-use tokens generated by an authorized service. This way, credentials for the object storage are never stored in the edge filers. As a result, backup is now secure.
CTERA is deployed within the customer’s environment, encompassing both on-premises infrastructure like VMware, and leveraging cloud storage solutions such as AWS S3, Azure Blob Storage, among others, to support availability across multiple regions and locations.
“We have built-in HA. So if any component fails, there’s a redundant system running in a nearby region,” said Saimon Michelson, VP of Alliances during a technical deep-dive session.
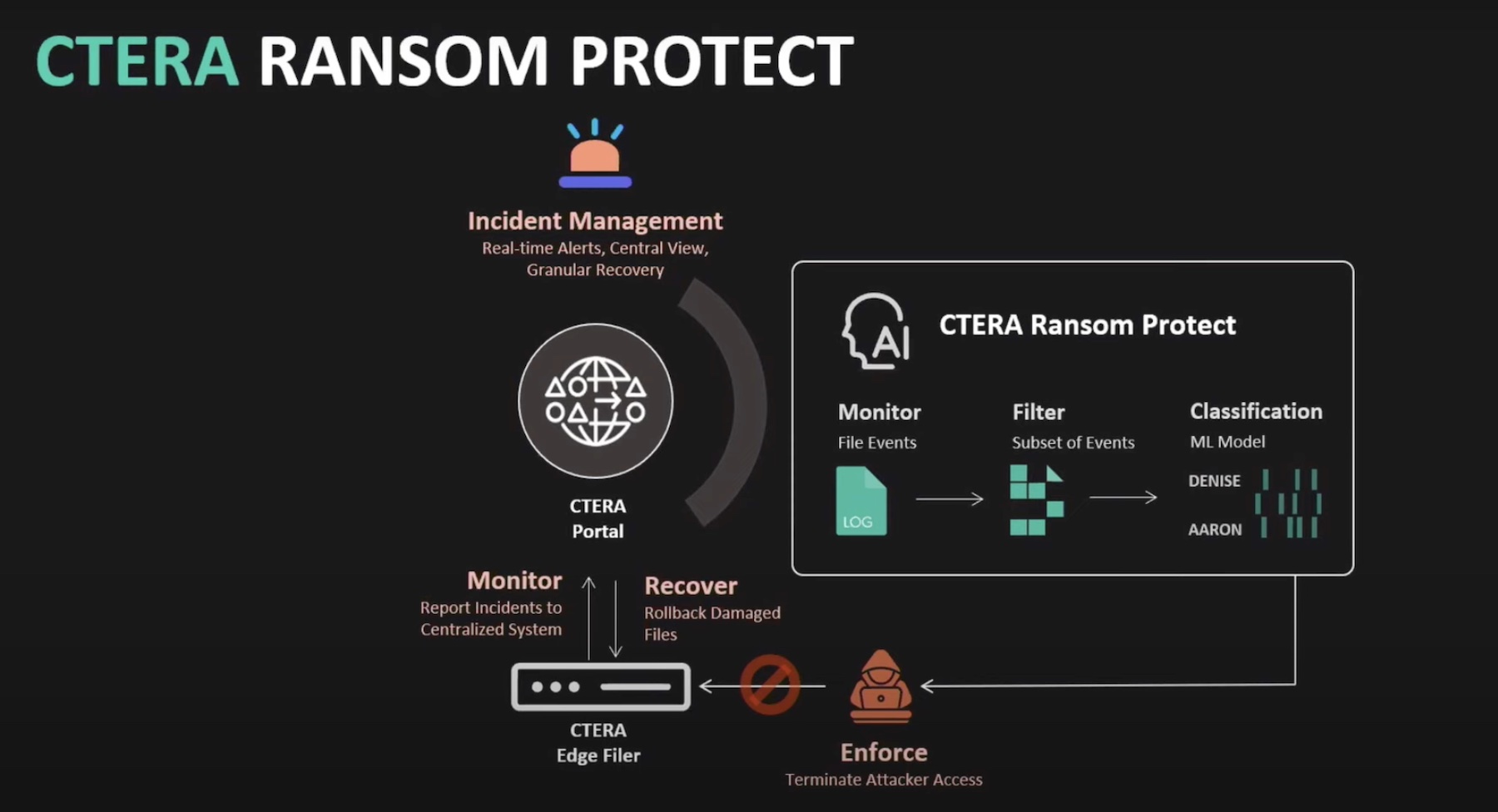
CTERA Ransom Protect
To ensure that a parallel trend is maintained even when ransomware enters the environment, CTERA now provides an early detection capability with the newly launched CTERA Ransom Protect. As noted, risks of exposure are abound in a network. For enterprises, there a couple key things that they should have in place in order to get a grip on mitigating those risks. One of them is early detection.
Ransom Protect identifies and isolates all suspicious behaviors and file activities, allowing administrators to launch a kill chain within seconds of the attack.
All malicious incidents and anomalies are recorded and logged as forensic evidence to aid post-attack analysis. Administrators can watch an attack closely from CTERA’s incident dashboard that displays all information about ongoing and past threats.
CTERA has built-in incident response that quarantines users and devices, cutting off their accesses within the first 30 seconds of the attack. But instead of blocking out the file shares completely, it lets authorized users continue to access them.
CTERA uses an AI-based engine that has ML algorithms working inside of it. But unlike other detection solutions, it does not rely on signatures to discover attacks. “Ransomware trends change quickly and there is no way to catch attacks with any level of accuracy with just signatures,” said Brand.
In the past, following the signature trail has ended in false negative results. “We found that many of the ransomware solutions that use techniques to evade the signature-based detection, even the known ones, used very common file extensions like doc and MP3, and they do things that look like normal activity. Therefore, we found this inaccurate,” he commented.
CTERA’s ML algorithms are trained with large volumes of data on standard and real-world attack behaviors and events. It is able to detect both known and unknown threats, and distinguish between suspicious activity and normal user behavior with high accuracy.
Ransom Protect is integrated in the CTERA Edge Filers. With a single click, the solution can be activated instantly. Running on the edge, it doesn’t require cloud access and being lightweight, it causes no impact on the system performance. Once activated, it is always on.
Michelson highlighted that users can set the controls to align with their organizational policy as required. “It’s looking at the entire volume but the unit of measure right now is an instance of an edge device. So, you can choose to enable this on one edge device versus another. We also have the capability to exclude specific users or groups, or schedule specific workloads that maybe, are problematic, and so on.”
Wrapping Up
A ransomware attack has the potential to hemorrhage a business impacting all lines of protection, no matter the size or scale of the organization. CTERA’s solution powered by the new Ransom Protect provides holistic security that a) makes organizations resilient against ransomware threats, and b) maintains an even protection posture, minimizing disruptions, and ensuring consistent access to data, without pauses.
For more, check out more interesting deep-dive presentations by CTERA from the recent Storage Field Day event.




