Organizations all over the world are getting hit by ransomware. A cyber threat report published by SonicWall states that over 300 million ransomware attacks were recorded in just the first half of 2021. Although the number tumbled slightly in 2022, attacks went back up in 2023 by a shocking 37%. The volume of double extortion and repeat attacks too is spiraling.
Zerto is one of the companies in the cybersecurity front that is keeping the fight against ransomware going with increasingly sophisticated security solutions. At the recent Security Field Day event in Silicon Valley, the company showcased two solutions within the Zerto Platform that isolate and lock data from bad actors, making recovery swift and unfussy.
Zerto’s Core DR Technologies
After an attack has run its course, it takes a tremendous amount of cleanup to get things back to the former state. It is a slow and punishing undertaking. Just conducting a thorough investigation alone takes weeks. The hardest part of all is to push the recovery efforts in a level-headed manner.
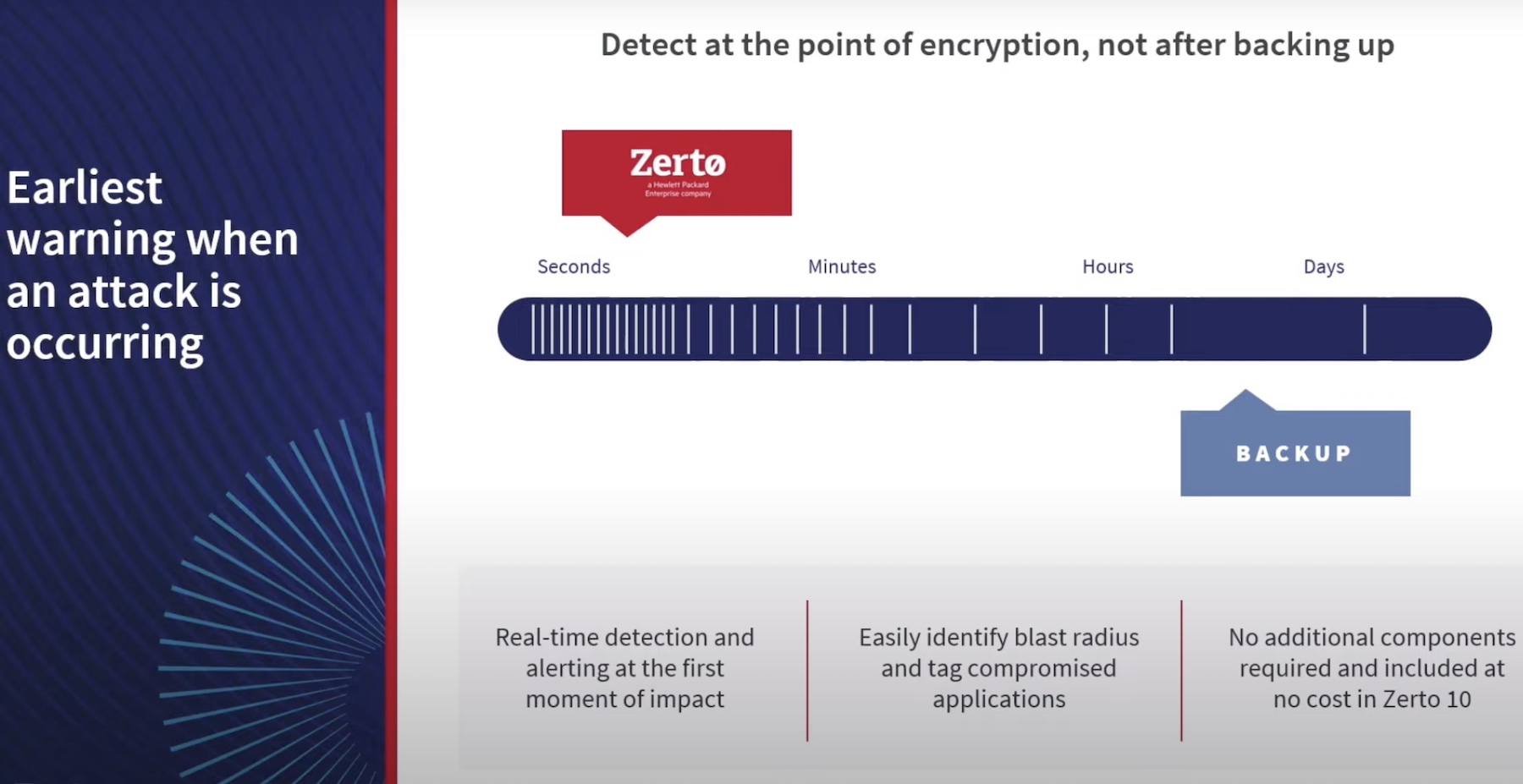
Zerto takes a proactive approach for dealing with ransomware crisis. It believes that there is value in keeping data in. As a disaster recovery solution provider, Zerto leans on data replication. Data is continuously copied and written to a storage in a secondary location. This allows granular recovery, ensuring little to no data loss.
To take it a step further and provide continuous data protection and enable recovery to any point in time, Zerto offers journaling as opposed to traditional snapshots. Zerto journals are dynamic logs of changes happening at the VM level. A user can set up the journal history to up to 30 days, and Zerto will automatically checkpoint the data at an interval of 5 to 15 seconds. Journaling tapers down the storage expense, which is typically high with snapshots, and allows full recovery of files to sites within seconds.
Zerto Public Cloud Isolation and Immutability
But once attackers make their way into the environment, they can seize control of the journals, and make recovery extremely complicated. So, as an extra line of defense, Zerto offers Public Cloud Isolation and Immutability. This capability produces immutable copies of the journals and saves them in public cloud.
The copies are taken straight out of production VMs, and therefore no impact is made on the workload performance.
“It doesn’t impact the production workloads because we are not stopping them to pause to snapshot. We are taking it out of a copy that we already own in our environment on a secondary or local site,” says Sr. Technology Evangelist, Chris Rogers, during the presentation.
This copy is secured with an object lock. “It’s your last line of recovery. It’s probably not something you are going to do every 10 minutes,” reminds Rogers, “But you can. It’s completely down to the customer.” The standard frequency is once every day.
Marked as immutable on a different format of storage, this repo comes handy when data needs to be recovered. The repo can be remounted to a clean infrastructure, where all the VMs can be pulled back from that point in time.
“In this case, the RPO will obviously be longer than a few seconds because Zerto is taking those copies on a periodic instance, but if you can’t recover using the journal, this is a great option, and it is relatively low cost,” he says.
This repo can be optionally disconnected to prevent infections.
The capability comes at no extra cost to the users. It is bundled with the Zerto license. The only thing they need to pay is for storage in public cloud.
Zerto Cyber Resilience Vault
The second feature is the Zerto Cyber Resilience Vault, a fully isolated, air-gapped and immutable data vault that keeps data safe from ransomware. Leveraging Zerto’s data replication and journaling technologies, the Cyber Resilience Vault is customers’ “last resort in worst-cast scenarios”.
“This isn’t bolting on other bits and pieces in our existing platform that we had. This is purpose-built for cyber recovery. The vault is for the most sophisticated and large-scale attacks,” says Rogers.
Unlike a backup appliance, the vault sits on a production-based infrastructure architected with HPE Alletra and ProLiant for storage and compute, HPE Aruba Networking, and the Zerto recovery software on top. “It’s not slow and low and deep-capacity. This is all-flash hardware.”
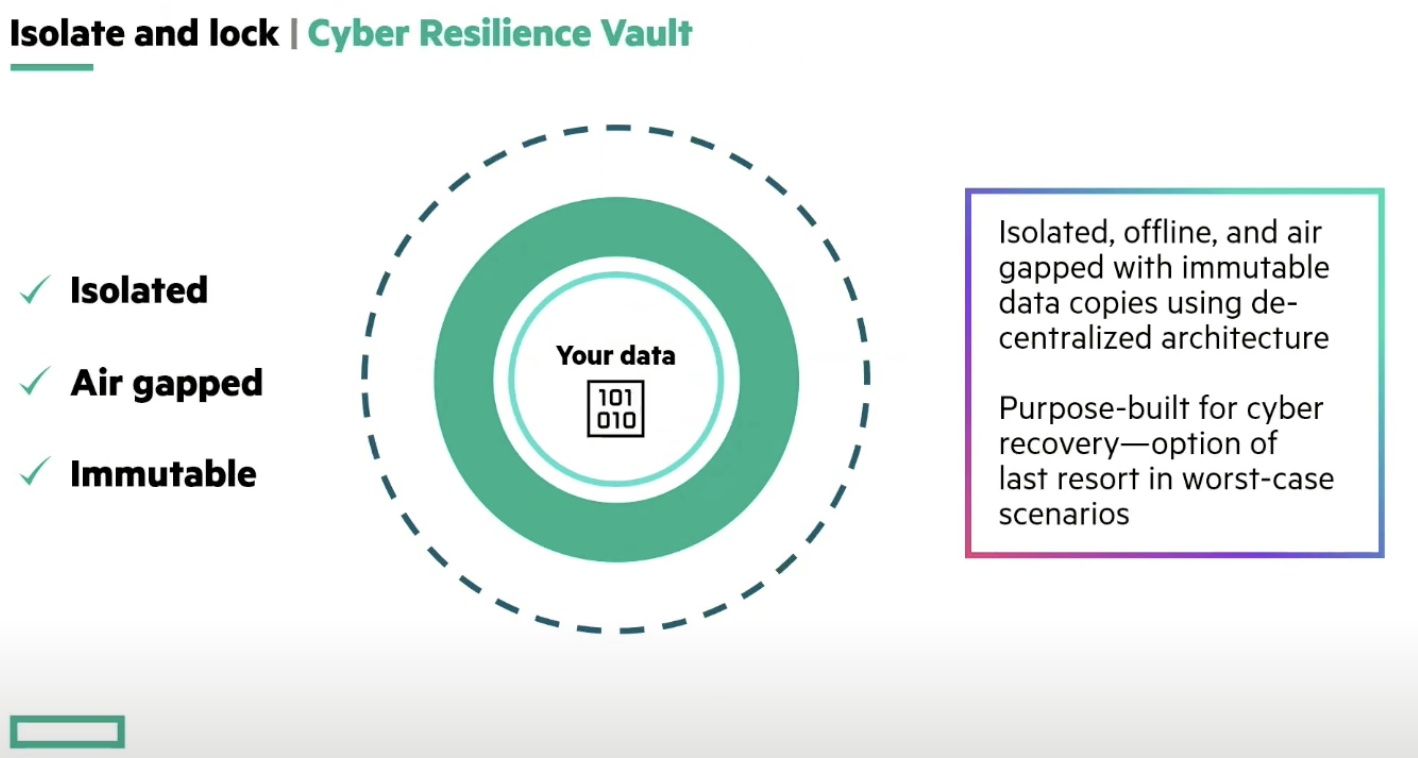
Rogers offered a quick peek of the architecture which comprises a landing zone to land the data in, and a collocated vault zone, which is a clean room where data is stored with no access to the Internet or the production network.
Restores are hands-off for maximum convenience. Located at the bottom left side of the UI is the Failover button that lets users start the failover by selecting the VMs or applications and the exact point in time they want to recover to. Zerto automatically sets up the VMs on the chosen storage on the network with the right IPs.
DR testing is undisruptive in Zerto’s on-demand sandbox. “We failover VMs while production is still running, in an isolated environment, then attach the replica disks to those, and create a scratch volume which is a temporary volume. Users can go can do whatever they need to do in this massive sandbox environment.”
Rogers informs that customers perform over 18000 DR and cyber resiliency tests in them monthly. The average RTO they experience is 3 minutes and 19 seconds, which is massively time-saving.
“We still maintain that 5 to 10 seconds RPO across all of those virtual machines that are testing at the same time,” says Rogers.
Additionally, the sandbox can be used for patch testing, vulnerability scanning, data analytics, and data forensics.
For more, be sure to watch Zerto’s in-depth presentations and demos from the recent Security Field Day event.