“What Lego has done for toys is what the microservices architecture is doing for applications,” said Tim Szigeti, Principal Engineer at Cisco, at the recent Tech Field Day Extra at Cisco Live US 2023 event in Las Vegas.
To put things in context, the IT industry is witnessing a great surge of microservices applications.
The case for Microservices architecture is built on the merits of scalability and resilience. Unlike monolithic applications that are built as a single unit, microservices software are structured as loosely coupled, but highly cohesive, self-contained services, that Szigeti referred to in his comment as Lego pieces that make up the applications.
Szigeti explained, “These applications are built using composable, interchangeable, interoperable microservices. You can mix and match and recombine them in a myriad of different ways – grab some code from open source and mix it with some internal code – connect to an external API, and you have got yourself a new app.”
Vulnerabilities Are Eating up Applications
A gargantuan explosion of application development has brought into market millions of microservices applications delivering on the promises of the architecture. But although microservices has upended the architectural limitations of its precursor, it has hurled new challenges at developers and security folks, the first of which is vulnerability.
“When the apps are so diffuse and distributed, our attack surface is wide and just exponentially exposed,” he said.
Microservices applications have inherently complex constructs. What makes the software architecture modular and granular, is also the source of its vulnerability. Data publicly shared by afflicted organizations show that 78% attack paths leverage known vulnerabilities, and software vulnerability is frequently the first point of a kill chain.
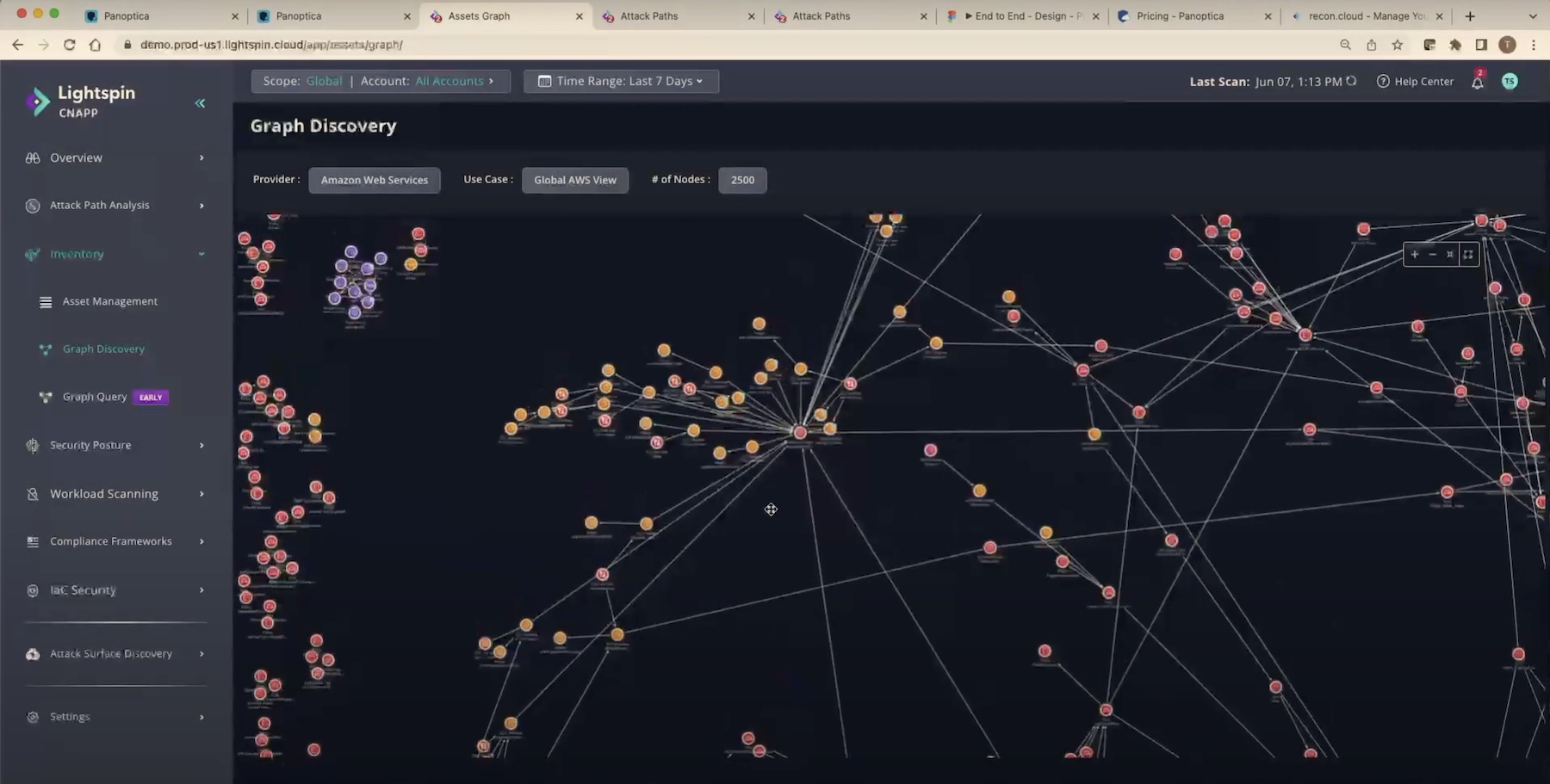
Szigeti visualized the anatomy of a microservices software with a graph. In the picture, a myriad of dots and lines represented the resources and their interconnections. Together, they made an elaborate and complex surface.
“If we have to protect the surface of something like this, as well as all the inner workings, interconnections and the software that these are composed of, we have a huge series of challenges on our hands. We need a new approach, a new type of tool,” said Szigeti.
But vulnerabilities don’t just reside within the fabrics of an application, but also in the software supply chains, leading to damaging and notorious attacks. In the past, companies have unwittingly deployed codes in their environment, that were compromised at source, setting the stage for nefarious breaches.
Cybercrime losses are estimated to reach $10.5 trillion by 2025. In contrast, organizations’ average budget allocation for security is only 1/3rd of the IT budget. A puny sum to counter the $4.3M that offenders have collectively extracted from their victims in one year.
“There’s an underestimation of exposure, and what is needed to be protected in our organizations,” stated Szigeti.
Thriving in a Perilous Landscape
How do organizations protect something as nebulous and complex as the attack surface of a microservices software?
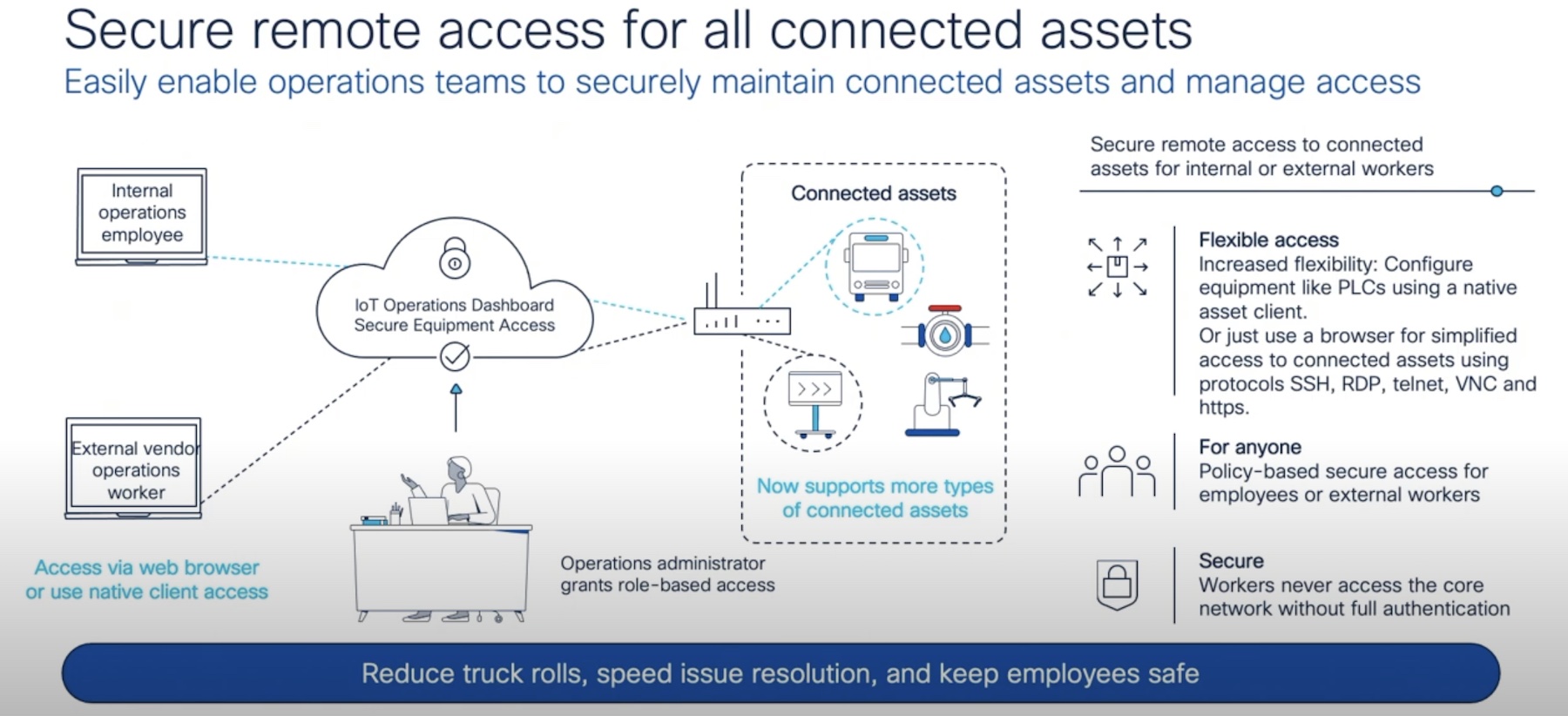
At Cisco Live US 2023, Cisco announced its cloud security solution – Cloud Native Application Protection Platform (CNAPP) in the keynote. Later, at the Tech Field Day Extra at Cisco Live US 2023 event, Szigeti elaborated on the capabilities of the solution and why it is extremely relevant to cloud security.
In March, Cisco acquired Israel-based cloud security software company, Lightspin Technologies Ltd. The acquisition fortified Cisco’s cloud security technology, appending new capabilities to CNAPP.
Szigeti’s presentation narrated how Lightspin CNAPP provides protection from the most vicious threat vectors, code to production. Szigeti says that protection has be layered across all phases, from development through runtime, as opposed to the common practice of enforcing security after the codes have been pushed into production, and letting the security team worry about compliance.
“The goal here is that if we can embed security-conscious decisions earlier in the process so that developers know that if they do so in a way that might come back to bite them later and they’re going to have to start over again, they do have the incentive of doing it right.”
Cisco adopts a three-step approach to tackle the complexity of this surface. Lightspin CNAPP secures the logic of the application, the workloads, and the cloud resources it runs on.
The combined platform, which is due to launch soon, will offer blanket protection against the worst attack vectors, aka, Log4j vulnerability, infrastructure misconfigurations – which have frequently been the cradle of attacks – privilege escalations, and generally very complex attacks.
The reinforced CNAPP platform leverages Lightspin’s underlying graph database technology that provides flexible querying and data correlations. The solution makes it a child’s play for operators to find sneaky threats – just type in the name of the component and the solution will scan and search all given packages, and upon detection, will show where the vulnerability is, and to what point it extends, visualizing everything with a blast radius map.
The platform approaches vulnerable configurations in the infrastructure the same way. Operators can look up any suspected security exposures by their specifics, or by selecting the type of exposures from a pre-built category. Lightspin CNAPP will search the environment for all public-facing elements. As it spots a publicly accessible asset that matches the category, it will highlight it with an elaborate risk report and recommendations for remediation. Users will have the options to remediate the issue manually or through CLI.
In the same way, Lightspin CNAPP can hunt down privilege escalations. The Identity and Access Management page offers a detailed report of suspicious accesses and steps of remediation.
Last but not the least, Lightspin CNAPP can reverse-engineer attacks by intelligently analyzing the attack paths, no matter how wildly complex, spotting threats and mapping out blast radiuses, putting the information in a single narrative for the operators to see.
Wrapping Up
When living in a cloud world, more than anything else, organizations need a clever, self-driving security solution that can perform all the steps of recognizing, analyzing and correlating vulnerabilities, instead of generating non-stop alerts and becoming a source of worry. The modern digital environments are full of noise and the last thing IT teams need is to be caught in an alert storm. Cisco’s Lightspin CNAPP does more than pointing towards a vulnerability. It highlights the criticality of that vulnerability, the past and present events that correlate to it, and puts together the steps to address it. IT team can now see the series of exploits that exist in the environment before it lead to the final attack.
For more information, be sure to watch Cisco’s demo of Lightspin CNAPP from the recent Tech Field Day Extra at Cisco Live US 2023 event, at techfieldday.com.