How many wireless IoT devices do you have in your enterprise? Do you even know? And if you said “zero”, are you totally confident in that number? The scary part of IoT is that no one can be. Internet of Things is a movement that has a lot of wireless and security professionals scratching their heads. How exactly are they going to deal with the explosion of devices out there? And once we know for a fact that we have those devices on our wireless network, how can we make sure they behave?
Internet of Threat Vectors
One of the scariest things about IoT devices is the fact that you don’t control them. Some industrial devices exhibit a high amount of configuration and control because they were not originally designed to be connected to the Internet. So the gateways that enable them have all the knobs and switches enabled for us to tweak away to our hearts’ content. But what happens if those switches are disabled?
As is the case in most consumer and prosumer IoT devices, lack of configuration options is done for the sake of simplicity. The fewer switches you have to enable the better the experience for the user. In fact, most IoT devices end their configuration at connecting to the wireless network. Once they’re programmed and connected to the network they only allow configuration through an app interface. Which limits our ability to see what they’re doing. Do you know what DNS entries your intelligent thermostat is using? Can you say for certain what it looks like when your systems are working correctly? Worse yet, do you know how to spot when they aren’t?
There are tons of apocryphal stories all over the Internet about sensors being compromised or IoT devices being made to redirect traffic to create a DDoS attack on specific targets. But one of my personal favorites isn’t about sophisticated hacker skills, but instead about laziness. There’s a wonderful story about a company that installed a network-enabled building HVAC system and also installed an on-site control server. Rather than creating a policy that required the management company to securely connect to the server via VPN it was instead decided to give them access via insecure RDP. And to keep it simple they just decided to open RDP to the entire world, not just one IP address range. You can imagine what happened next in the story.
Fixing Faults with FortiNAC
If you want to truly solve the IoT problem, you have to solve it in the medium that makes it the Internet of Things, which means the network. During Mobility Field Day 4, I had the chance to check out some of the latest offerings from Fortinet. One that really caught my eye was their FortiNAC solution, outlined in this video by Chris Hinsz:
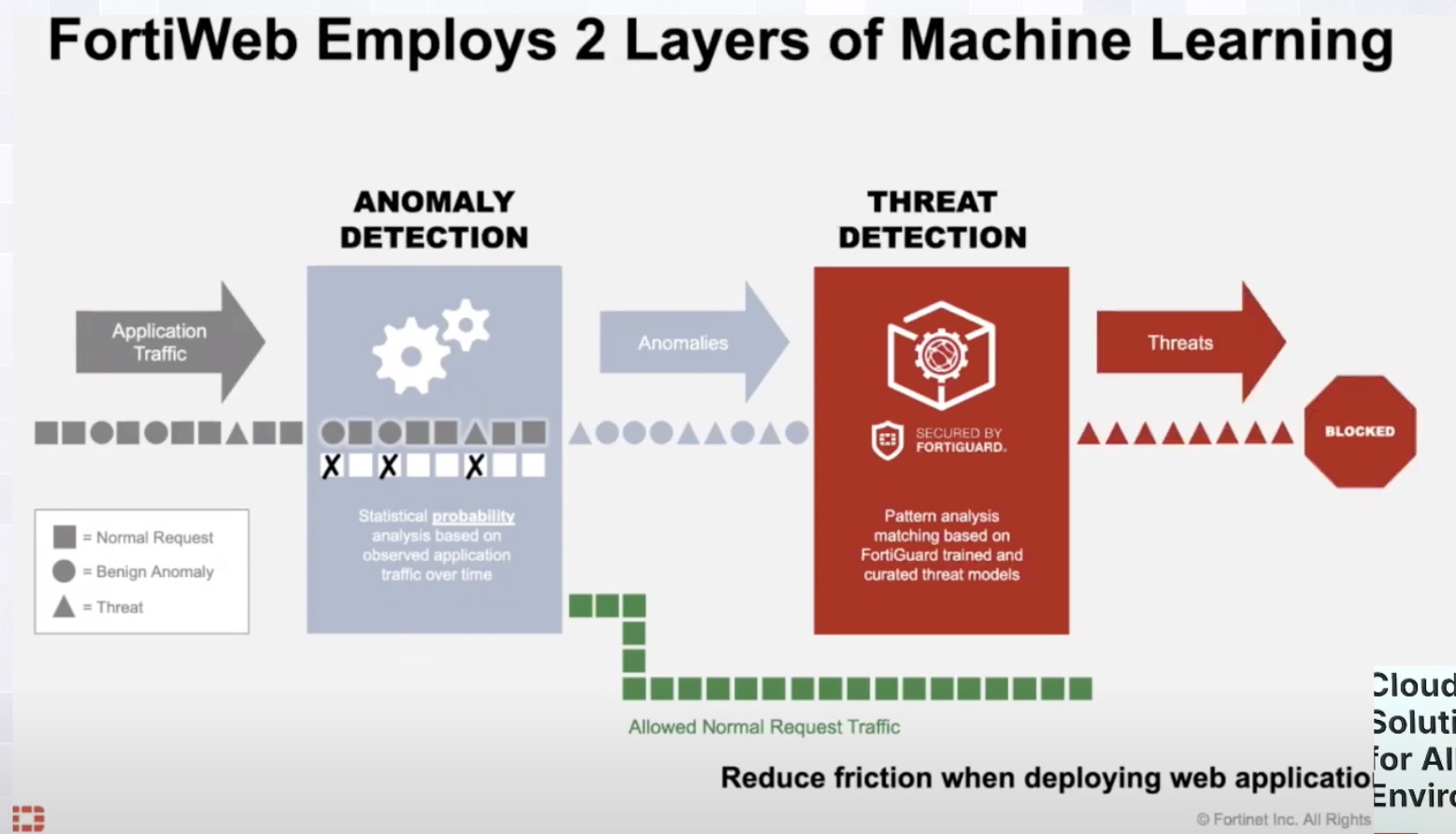
FortiNAC tries to accomplish the things that need to be fixed with IoT in what I consider a novel way – traffic profiling. NAC solutions have always been a little dodgy when it comes to user-based traffic because of how uneven it is. Users that normally might do web-based traffic browsing might be asked to upload a lot of videos. To the NAC solution, this looks like data exfiltration. So it may lock down that attempt to actually get your job done. Which frustrates users and causes all kinds of headaches for the security team.
However, IoT devices aren’t quite as flexible. They have known communications addresses. They have regular data patterns and amounts. You know what a device should be sending and where it should be sent. So you know what to look for with anomalies. And you can set triggers for any behavior that occurs outside of those parameters. And that can be hugely important when you catch behavior outside the norm.
Think about a hospital environment. All those medial monitoring devices are IoT devices that have specific parameters they need to follow. MRI machines will send huge picture files to servers to be read later. But they should only send those files to one or two locations. If you’re tracking the network activity of that particular device and you see it sending data to another location you are probably going to raise an alarm, right? How about if that device starts getting data from other locations aside from the MRI scanner? Another red flag. But you won’t know that from the machine itself, or more accurately the workstation attached to it. That’s the power of a solution like FortiNAC. You can see the behavior of the device in question without needing to have an agent or even a peek into its configuration.
The breed of NAC solutions that are needed to observe IoT devices requires a bit more horsepower than those in years past. You need to be able to see the traffic from the device as it’s flowing without any hints from the device itself. It’s almost like tapping the network to ensure behavior. But, more importantly, the NAC solution needs to be tied into the network itself to be able to isolate the device is policies are violated. Before, this was a simple as having the device agent shut everything down until the violations could be figured out. But now, with the inability of the solution to install agents directly on the device, the NAC solution needs to find more creative ways of dealing with those communications.
To me, that’s why FortiNAC is so important. Because it integrates with the new edge that is wireless networking. IoT devices don’t have room for Ethernet ports or other unnecessary connectivity. A wireless radio is all that’s needed to get them online. And if your NAC solution isn’t integrated with the wireless network you’re going to have quite a time trying to enforce policy at the edge. Fortinet does a great job of putting their NAC solution together with their wireless controllers and their edge firewall capabilities to create an all-in-one solution that fits a wide variety of customers.
Bringing It All Together
IoT is scary because it lacks the kinds of controls that networking and security folks have become used to over the years. There’s no way to open the hood and peek underneath. Instead, we’re going to have to start thinking about securing these devices in a different way. Solutions like FortiNAC go a long way toward helping us profile the behavior of those devices and ensure they aren’t representing threats, either to the wireless network or to the wider security posture in the enterprise. That’s something that will help any security department figure out the best path forward that includes IoT.
For more information about Fortinet and their FortiNAC solution, make sure to visit http://Fortinet.com.