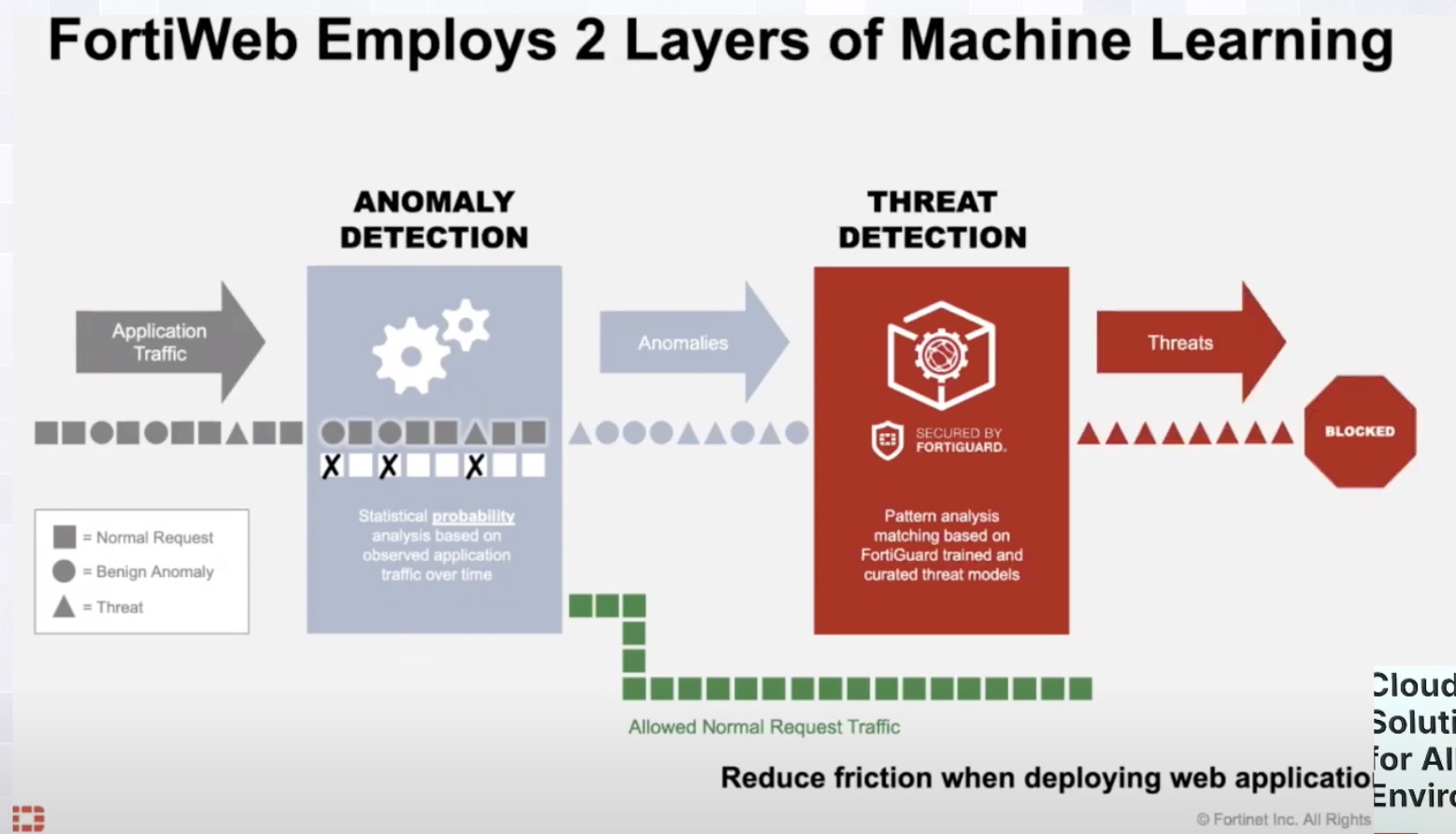
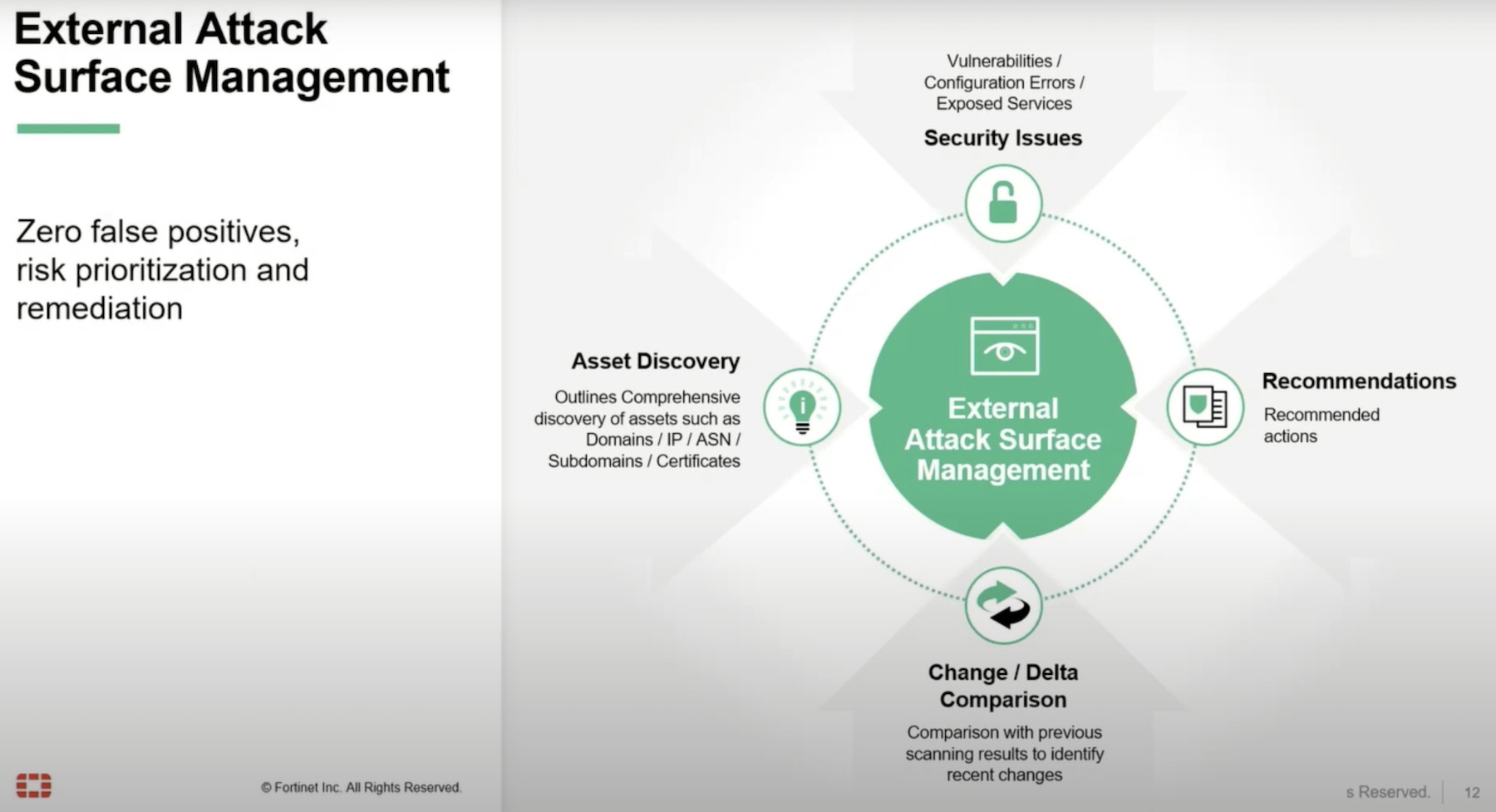
Security is all the rage today, isn’t it? Every time I open my news reader I see stories about breaches and exposures and vulnerabilities that need to be patched. It’s a buffet of unhappy work that I’m going to need to clean up or worry about outside of the normal woes of providing access for my users or ensuring the cloud doesn’t go down this week.
Security isn’t just a piece of duct tape that you can strap on to a platform after the fact and hope that everything is going to work out. It’s an integral piece of the puzzle from the very beginning that needs to be accounted for. Why? Because if you try to cover your security holes after the fact you’re going to miss something. But if your security solution is built-in from the very beginning you can’t ignore it.

Wireless and networking are two transport technologies that are starting to become one integrated solution in the mind of those that support their user base. To the users, wireless isn’t a different technology than the network. It is the network. No one drags an Ethernet cable from office to office to stay connected now. Likewise, when someone needs to hook up a new device to support a user, like a printer or some IoT gadget, wireless is often the only way to make it work. Trying to treat wireless and networking as two different technologies today isn’t going to get you very far with the executives.
So why do we try to treat networking security and wireless security as two different topics then? Sure, wired networking has certain needs for security like firewalls and intrusion systems. And wireless needs security to encrypt data packets in the air as well as detecting rogue devices in your air space. But once the packet hits the access point it becomes a wired network security issue too, right? Why are we still drawing a line between what wireless security does and what wired security should do?
The First Line of Defense
During Mobility Field Day 5, one of the presenters was Fortinet. They have a long history in the security space. I can remember using their firewalls all the way back in 2006 to help secure my school customers. Today, they have a lot of other solutions, including wireless access points and controllers and SD-WAN appliances. What’s the difference between their solutions and others?
Fortinet is a security company first and foremost. Their patented ASIC technology exists in everything they make. This means that security isn’t bolted on. I would like to call your attention to this great session from Ben Wilson on the vision they have for wireless:
Notice how they don’t call it a wireless network. They call it a Security Fabric. That’s an important distinction for me. Because it means that Fortinet doesn’t draw that line between the packets flying through the air and ones racing down the wire. They are one and the same to Fortinet. This means they are protected the same way with the same policies and protections from origin to destination or exit from your system.
What does a unified security fabric mean for you? It means not worrying about what happens when traffic needs to be decrypted from one medium to another. It means not needing to worry that your accounting data is traversing the wire in cleartext. It means voice calls are safe from a mobile wireless handset to the other caller without being snooped upon. It means that even the least security-aware person in your organization is treated the same as the most paranoid security researcher you employ, at least from the perspective of the network.
More importantly, it means that you don’t have to worry about configuring a whole bunch of bells and whistles in your system either. Because the security is baked in, it’s already enabled. Want to make your authentication more secure for internal users? Done. Now they need to use Active Directory to get on the internal network, both with wireless and wired access policies. Need to provision a secure network for your contractors? Lock it down as much as you want and enforce whatever policies you’d like. They’re bound to that network and they won’t see anything you don’t want them to see. It’s simple and easy and can be reconfigured over and over again for any technology you need to support. And because it’s all integrated, you won’t forget to enable it.
Bringing It All Together
If you’re a physics nerd like me, you know there is a hunt for something called the Grand Unified Theory that postulates that all forces in nature are just aspects of one single force. We have been searching for that force for decades and, while we haven’t found it just yet, we have been able to determine that several forces are intricately linked all the way down to the basics. I truly feel that wireless and networking have reached that point in our understanding of connection technologies. And with the help of companies like Fortinet, I also believe we’re going to find out that security really is just another aspect of connectivity.
For more information on Fortinet and their wireless and security technologies, please make sure to visit their website at http://Fortinet.com/