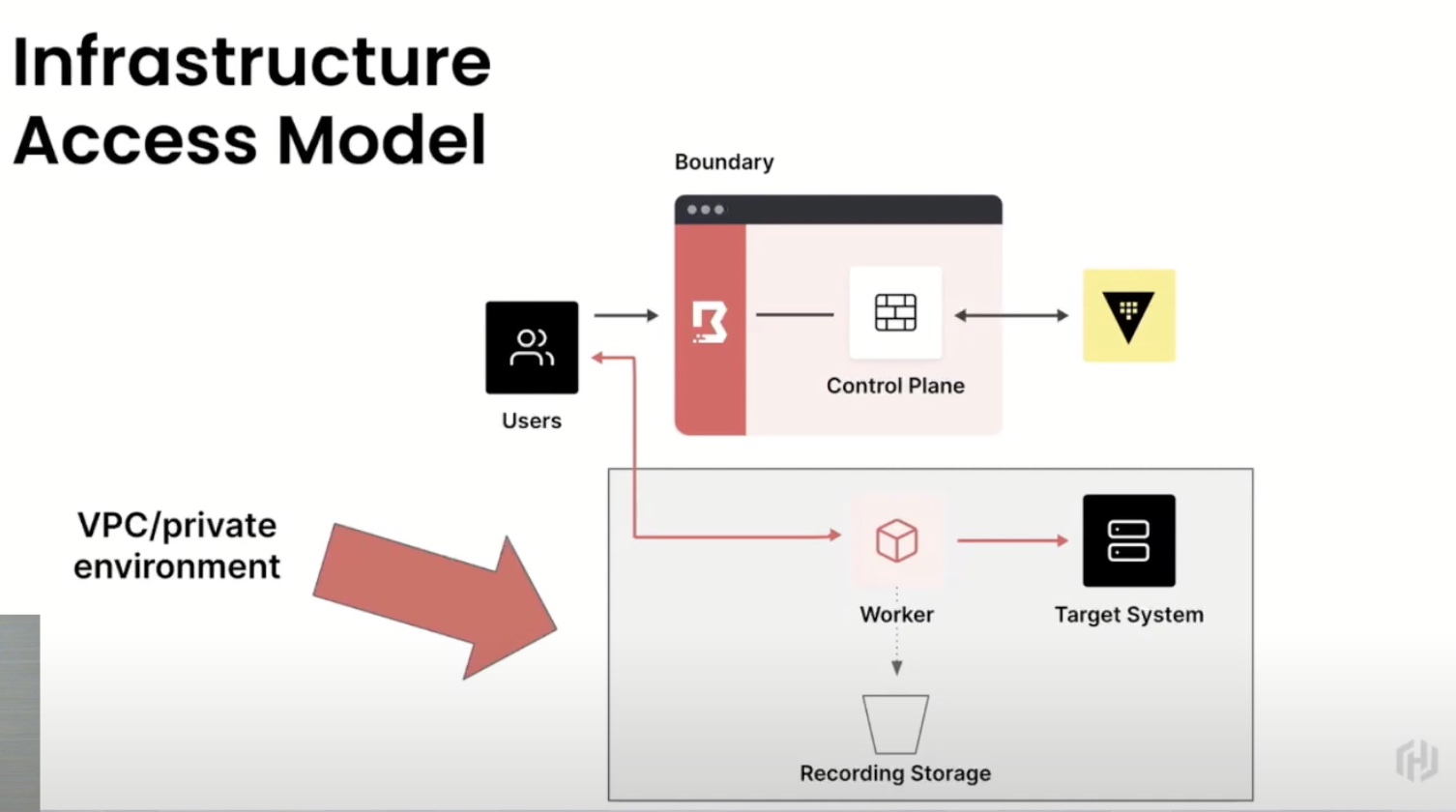
Although viewed by some as another marketing buzzword, the concept of zero trust security is one that can help many organizations to better control and secure their users and environments. Though no security tool is a silver bullet, the triad of solutions displayed by Hashicorp at March’s Security Field Day offers a way for enterprises to integrate a zero trust framework into their environments.
Establishing Zero Trust in the Enterprise
With so many potential threat vectors aiming at today’s enterprises across multiple cloud and on-premises environments, their IT departments need to find a way that they can lock down all of their crucial resources while still enabling easy access for end-users. Zero trust security is quickly becoming one of the top methods today to do so.
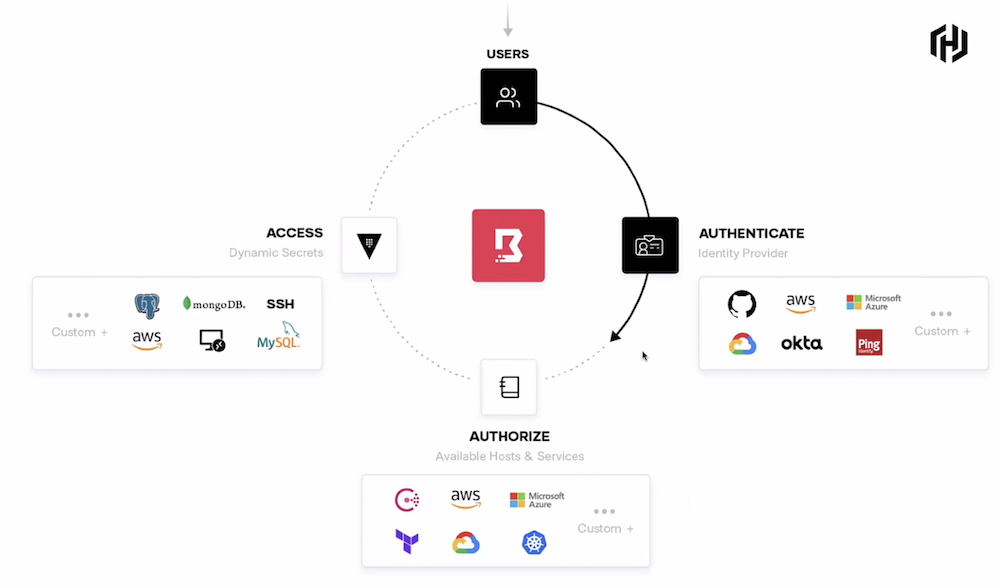
Zero trust is predicated on the concept that IT staff trust nothing and verify everything, authenticating and authorizing access at all points. Users then build trust to show they are worthy of accessing resources through credential logins and other key security measures like multi-factor authentication. In practice, zero trust security is dependent on these four basic identity-driven controls, as seen in the image below:
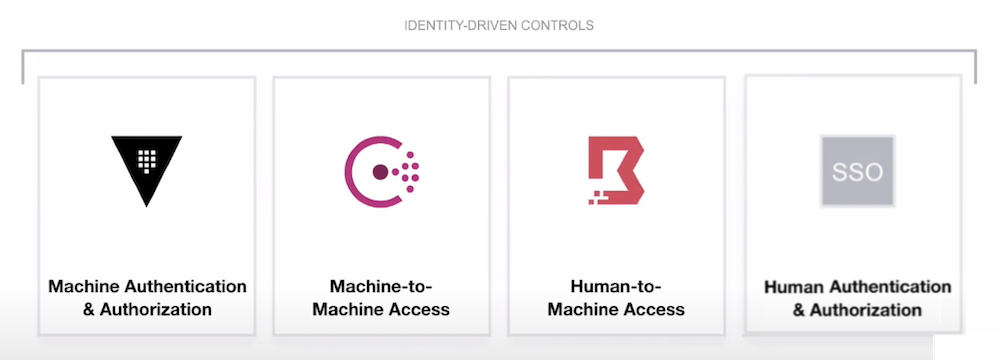
When all four of these primitives are accounted for, IT admins generally have tight enough control over their environment that they can ensure only the right people are accessing the right materials with no exceptions. However, anyone who has attempted to implement zero trust security in their organization may know that spinning up each of these four criteria can be difficult. With a myriad of different security solutions out there, integrating one for each primitive into an environment and then integrating all four together is a real hassle.
Hashicorp’s Zero Trust Security Portfolio
Hashicorp, creators of the popular Terraform coding software, believe they have the product portfolio to tackle IT organizations’ zero trust needs. As you may have noticed in the image above, the first three identity-driven controls have a corresponding graphic. Those are each members of Hashicorp’s security product portfolio: Vault, Consul, and Boundary. Let’s explore each one and how it fits into the zero trust security model.
Vault
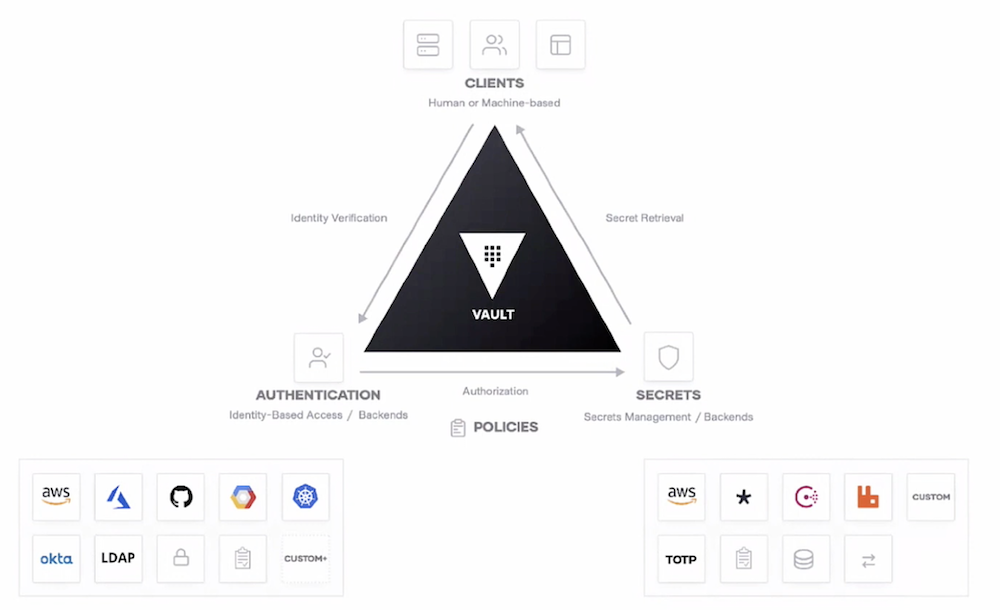
Hashicorp Vault authenticates and authorizes access between machines, using a three-step process of verification, authorization, and secret retrieval that can be configured using Policies, much like how GPOs work in Active Directory. Vault is an identity broker; it ingests the various forms of identity a user has and leverages them against an organization’s Policies to approve or deny access to secrets.
Once a specific Policy is set in Vault, a user or machine can request access to a particular secret and, once their identity is verified, are then moved through the workflow of obtaining said secret. If an attempt is made that is outside of a configured Policy, that attempt is denied access.
Consul
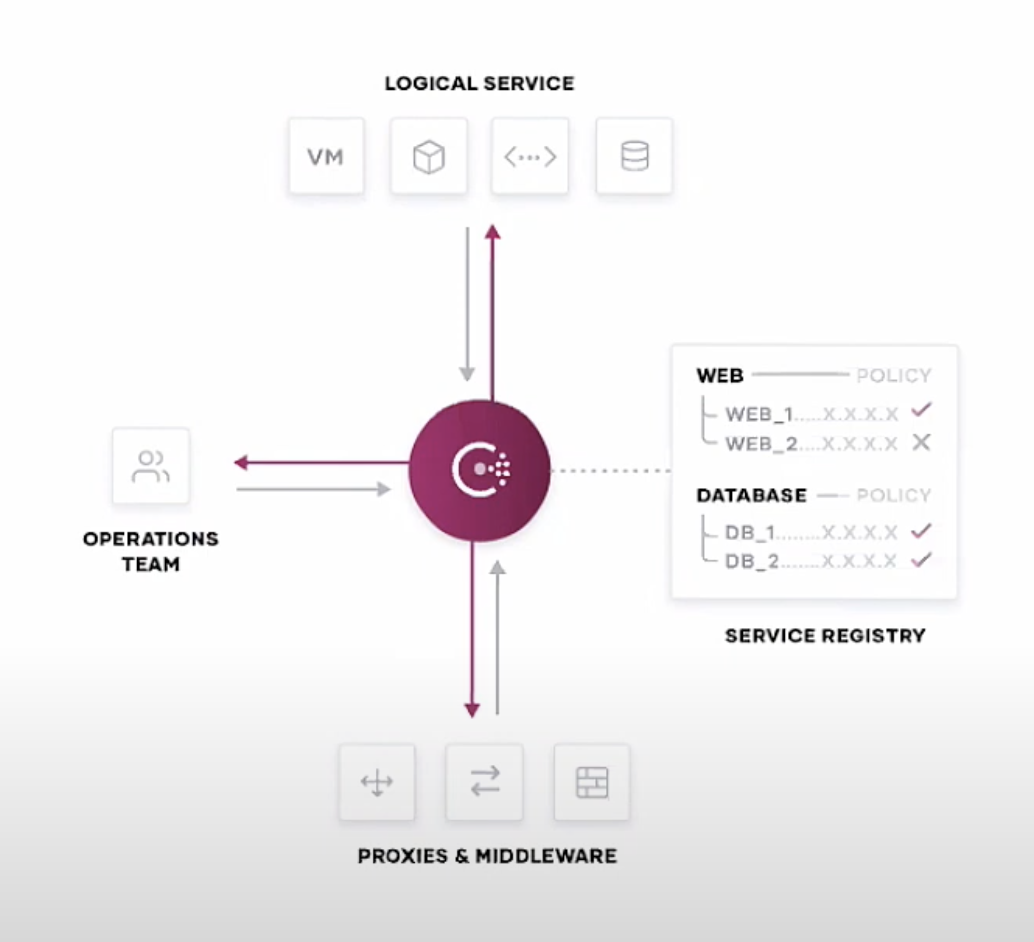
Hashicorp Consul takes a step further into access privileges, honing specifically on interactions between machines. In practice, Consul acts as a hub between Ops teams and their codebases, middleware, and compute, ensuring those network connections are both automated and secure.
Consul relies on three core workloads to operate. The first is service discovery and health monitoring, ensuring that all applications across an organization are both functioning properly and communicating with the other services they need to interact with. The second is creating a service mesh across an organization’s platforms, leveraging mutual TLS to ensure secure communications between them. Finally, Consul provides networking infrastructure automation, streamlining network processes so admins can focus on less tedious tasks.
Boundary
Hashicorp Boundary controls the interactions between humans and machines, leveraging existing identity providers and their preset authorizations to enable secure, remote access. With Boundary, traditional onboarding processes that require time-intensive authorization configurations are streamlined through role-based access controls.
Instead of manually adding users to the services they need, Boundary takes the user’s established identity, leveraging the access rights their role or department are allowed, and grants them access to those services seamlessly. That way, instead of exposing that user to your whole network, they only have access to the minimum amount of resources they need to get their job done.
Integrating the Hashicorp Portfolio for Zero Trust Security
In their appearance at Security Field Day, Hashicorp’s Director of Product Marketing, Chris Kent, detailed how each of the three solutions work together in tandem alongside existing identity management solutions.
Because they are all under the Hashicorp umbrella, Vault, Consul, and Boundary have pre-built integrations with each other, keeping identity consistency between the users and machines involved with their processes. They also all integrate directly with many of today’s top identity providing services, including web app single sign-on (SSO) and core directory services.
With all four primitive identity-driven controls covered, IT organizations have a unified approach to managing and securing access through Hashicorp. All they have to do is implement their controls and policies based on role/department, using the principle of least privilege to limit access to only what is necessary.
That way, in case of a breach or insider attack, the potential attack vectors available to that bad actor are reduced dramatically, also reducing the effects of the breach. This is truly an embodiment of the “trust nothing, verify everything” tenet that is core to a zero trust security model.
Zach’s Reaction
I am a huge proponent of zero trust security, and seeing what Hashicorp’s solution portfolio offers through ease-of-use and security coverage, it seems like they will provide a low barrier entry into the zero trust space for a variety of organizations. I would not be surprised to hear more from Hashicorp at a future Security Field Day event, touting the popularity and success of their product trifecta.
To learn more about Hashicorp’s Vault, Consul, and Boundary, you can watch full-length demo videos from their Security Field Day presentation, or visit their website for additional info and documentation.