Companies around the world have lost millions of dollars to cybercrime. Cyber attackers arbitrarily target organizations and paradoxically, despite being copiously armed, every day a new company falls prey to their attempts of infiltration. At the Mobility Field Day event in July, Betacom presented Betacom 5GaaS, a private 5G network with built-in security capabilities that gives companies a secure and private space to conduct business.
The Next Frontier is Private 5G
The public internet is teeming with security risks and that makes protecting data challenging as it travels from one point to the next. In the face of newer and more sophisticated strains of threats and heightened frequency of attacks, a private network makes a lot more sense simply because it is isolated and untouched by the public network.
Sadly, options like VPN that have existed a while now aren’t always the most logical recourse as these networks have become more complex with the years, and haven’t quite kept up with the changing technology. A better and more affordable alternative would be a private 5G network – private so that internal resources cannot be viewed, modified, or damaged by external actors, and 5G because it allows for ultra-low latency, secure connectivity, and reliable performance.
Betacom’s 5G as a Service
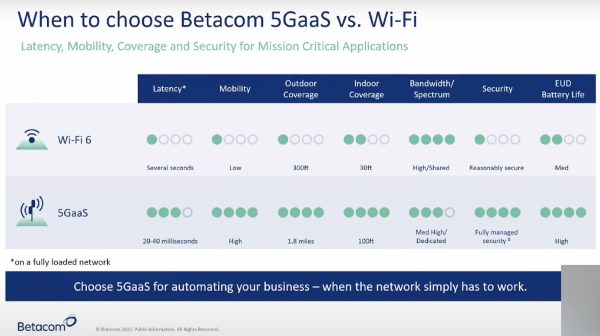
Betacom offers 5G as a Service that hits the sweet middle spot of medium dedicated bandwidth with great indoor and outdoor coverage, and high data rate and low signal interference. In terms of what’s better to use, 5GaaS or Wi-Fi, Betacom argues that a private 5G network makes a lot more sense than Wi-Fi, especially when there are mission-critical applications involved that requires ultra-low latency to run.
Betacom’s 5G as a service is a four-part service. For network of any size, work starts at the planning stage where engineers at Betacom draft a network plan picking out the various components that would go into it. At the design stage, things get a little more nuanced. The engineers decide the placement of the devices and APs based on the square footage of the premises. Planning and designing are based on factors like the use cases, number of access points required, the devices that the network would likely be serving and such things. This follows the installation process where all the hardware is installed and connected to each other on premises.
Betacom has a 24/7 fully managed operation service delivered by the security support center in Bellevue that manages network security 365 days a year.
A Zero-Trust Architecture
The Betacom 5GaaS boasts of a zero-trust architecture. Asad Vaince, Sr Director, 5GaaS Solution Engineering, Betacom says, “Our entire network resides within the enterprise firewall.” The core network which is built to the required size fits inside a small closet. The private core network connects to the RAN (Radio Access Network) through category or fiber cables. The fabric includes indoor and outdoor radios for wireless networking that can be mixed and matched with the rest of the components. 4G and 5G radios allow enterprises to start with a 4G deployment and upgrade to 5G as they go.
Access to the private network happens in two ways. First, through authorized SIM cards embedded in the connecting devices, this can be physical or electronic. This way, organizations can be certain that the devices connected to the network have clearance to do so.
The second method is through an IoT gateway. For legacy end devices, Betacom is working with vendors to have their devices natively embedded with CBRS or 5G chipsets. For the time being, Betacom lets devices that do not support 5G chipsets connect via its IoT gateway. The IoT gateway in this case assigns the device an IP to the CBRS signal into Wi-Fi or ethernet so that devices can access the network.
Security on a Fully Loaded Betacom 5G Private Network
At the Mobility Field Day event which took place in Silicon Valley, Betacom presented the Betacom 5G as a Service. Vaince gave a presentation of the Betacom 5GaaS and its security features. To set the stage for the presentation, he opened the talk with 5G and busted some common myths and hypes giving the audience a clear understanding and setting the expectation.
Accessible through SIM cards and multi-factor authentication, the Betacom 5GaaS network is highly secure and gives organizations full control. While the SIM card-only access is quite secure in itself as they can only be granted only from the inside, for extra measure, Betacom lets these cards be activated and deactivated instantly.
Secured with a zero trust architecture, the Betacom 5G network is private in all sense of the term. Since all of the network assets practically live behind the firewall, enterprises can set up their firewall based on their enterprise policy. They can decide and control what data or application gets out of the network and what stays in. This whole process can be encrypted end-to-end.
There is also a physical side to cyber-attacks that enterprises can fight against internally. Stopping malicious actors from physically accessing network equipment is half the battle and enterprises can win it by just enforcing its own security policies internally. Betacom facilitates that with the on-prem solution that allows organizations to keep it on premises.
Wrapping Up
The public internet serves as a stage for countless transactions and exchanges every day. Despite that, security was never something that was designed into it. As a result, it does not agree very well with how we use it today and that has opened doors for hackers and unscrupulous users to come in and access data at will. Betacom’s 5GaaS surely solves that problem by isolating the business network from the public internet and averting its many risks making a safe space for business operations and transactions. Cherry on top, it’s affordable and more reliable than the other alternatives.
For more information on Betacom 5GaaS, check out their other presentations from the recent Mobility Field Day.