Criminal groups and nation-state threat actors understand that data is the essential asset for organizations and states. Whether the intent is data theft, ransom extorsion, or irrecoverable data destruction, organizations are facing increasingly sophisticated attacks.
In the past years, and putting aside ransomware attacks, IT professionals have watched in awe as threat actors have launched bold moves such as supply-chain attacks, going as far as embedding mysterious chips on the motherboard logic of a hardware vendor according to a controversial bombshell report, or breaking through a respected monitoring software vendor’s chain of trust to embed malicious code in software updates.
In addition, security researchers keep finding vulnerabilities at an alarming pace, not only in software, but also in hardware components.
Keeping Up the Pace
To effectively address sophisticated cyber threats, organizations need to protect data and systems, enhance cyber resiliency, and overcome security complexity.
However, many organizations face challenges with their existing hardware infrastructure. Datacenter environments are often heterogeneous in nature – the co-existence of multiple hardware generations adds an extra touch of spice to the melting pot of vendors, technologies, and hardware components.
Managing these fragmented environments is complex and time consuming. As a result, implementing corporate or governmental security frameworks and strategies requires extensive preparation, followed by tedious and protracted manual labor.
“Modern cybersecurity should be intelligent, scalable, and automated.”
The Case for Holistic Security
While the challenge of complexity cannot always be fully eliminated, the fastest path to reduce complexity and strengthen the security posture is to evaluate vendor ecosystems that offer a holistic, zero-trust architecture across their portfolio.
Secure infrastructure ecosystems should include:
- a common embedded security foundation across hardware components such as servers, storage, and networking, also including hyper-converged infrastructures
- continuous, end-to-end threat monitoring backed by machine learning
- cross-stack secure data protection with data immutability and inviolability
- a secure software development framework with threat assessments and safety checks through the software development lifecycle
Individuals evaluating those criteria should ensure to select modern, resilient, and automated solutions. Modern infrastructures no longer rely on silos but expand from core data centers towards the edge and clouds with varied consumption models. The solution portfolio should embrace these hybrid approaches.
Resiliency relies upon the ability to build components in a fully integrated fashion, under supervision, and with the assurance that the entire supply chain is secure. Finally, intelligent infrastructure should be backed by artificial intelligence and machine learning. The infrastructure management component should holistically monitor the environment to detect early threat signs and thwart potential attacks.
Dell Trusted Infrastructure – A Zero Trust Approach
Dell Technologies has recognized the need for holistic, zero trust security across the entire infrastructure stack. An outcome of this acknowledgement is the adoption of “secure by design” principles which are applied across the entire portfolio, both on hardware and software solutions.
The cornerstone of this approach relies on building a resilient supply chain where security, integrity, and quality are essential considerations. Security is applied to information, personnel, and physical spaces as well as for Dell suppliers and partners. The entire product development process is validated from a security perspective from the initial concept all the way into physical mass-production, including integrity checks and quality assurance processes.
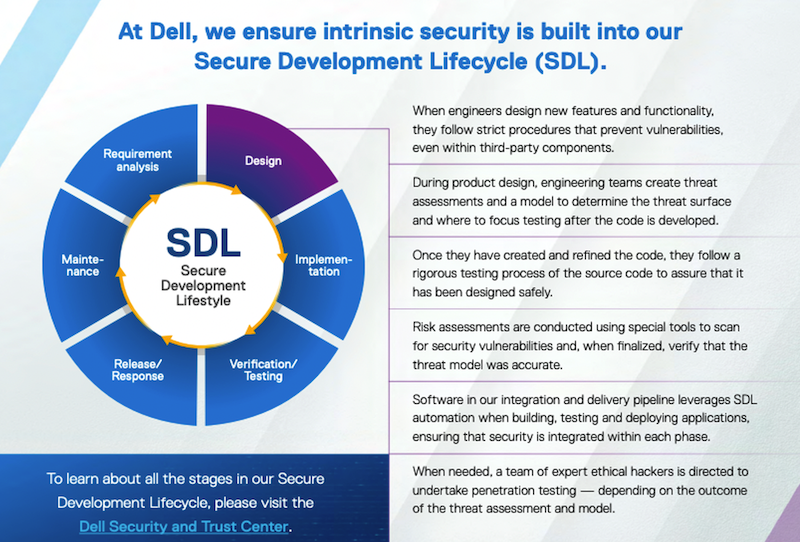
In addition, all products follow the Dell Secure Development Lifecycle (SDL) framework, as depicted in the infographic below. Development processes include strict procedures to avoid the introduction of vulnerabilities, threat assessments are created, code is tested, and risks are assessed. Identified risk areas are then addressed and if necessary, penetration testing is also performed. Finally, updates are digitally signed to ensure the chain of trust is maintained.
Exploring Dell Trusted Infrastructure
In addition to foundational security principles such as Dell SDL and secure supply chain measures, Dell Trusted Infrastructure consists of specific security capabilities embedded into each product class. Some of these capabilities also span across multiple components. Worth noting, many of these capabilities follow NIST security guidelines.
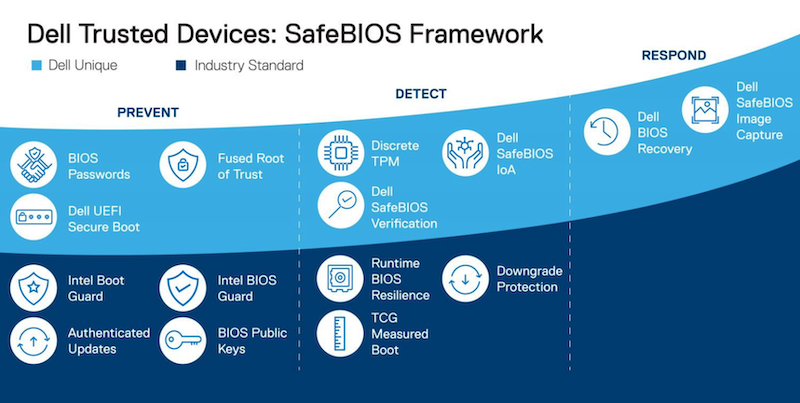
BIOS Protection
Dell PowerEdge servers include silicon-based security and cryptographic hardware root of trust (HwROT) to authenticate server booting and firmware upgrades. Read-only encryption keys are burned in the silicon microchips used in Dell designs. These keys cannot be altered or erased and are used at boot to verify that the BIOS code is legitimate. The technology is used to significantly mitigate risks such as undetected BIOS modifications or the ability for pre-boot malware to run. In addition, unauthorized BIOS and firmware code will simply not run. Those server-level capabilities also extend to HCI infrastructures.
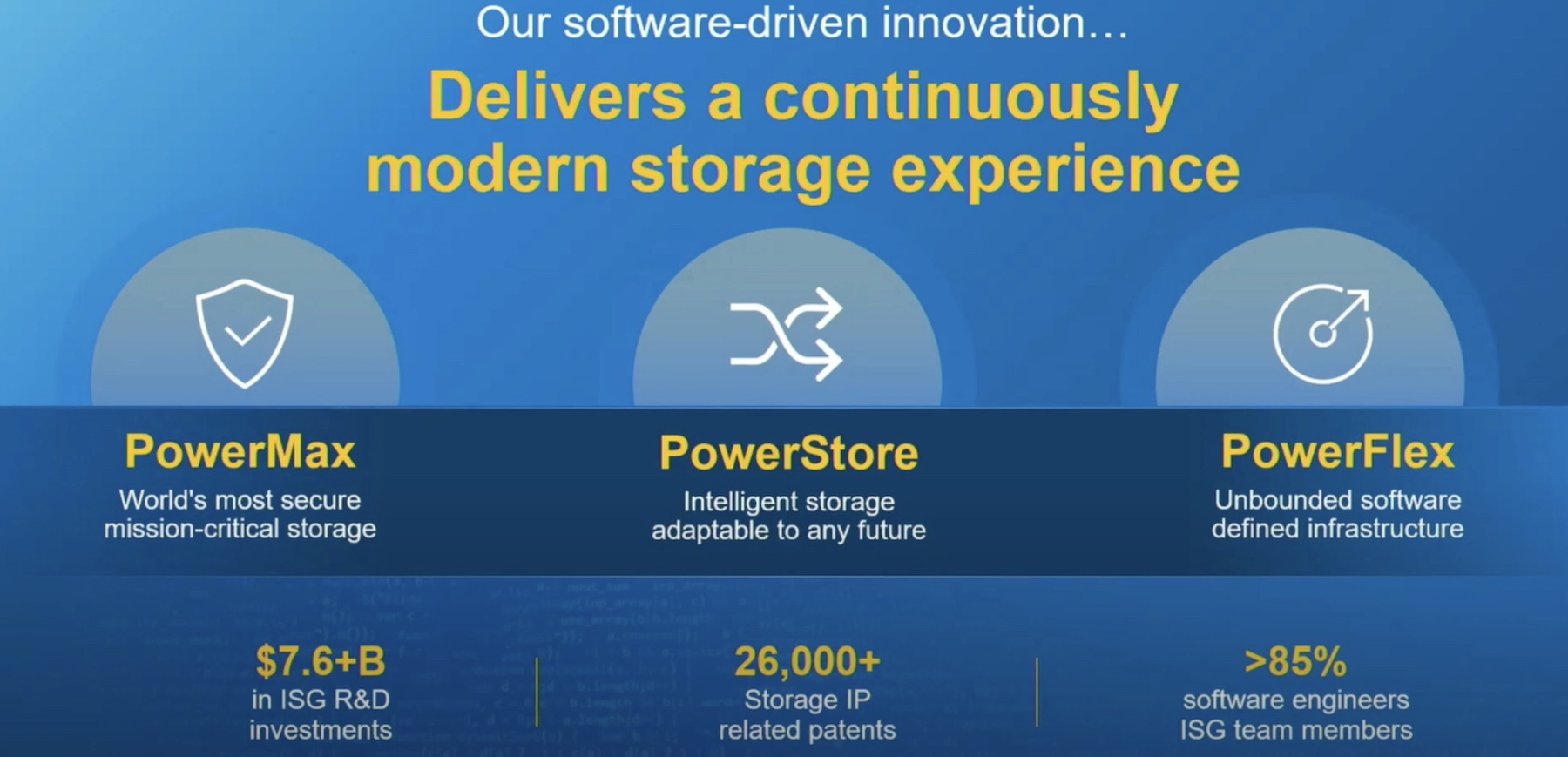
Storage Security
The HwROT technology described earlier also protects Dell storage platforms such as PowerStore, PowerScale, and PowerMax. HwROT is included at the disk array and fabric levels, a key differentiator with Dell’s competition. Additional capabilities include support for NSA Top secret grade algorithms, to support their longer service life, but also file monitoring & locking, ransomware prevention, integrated virus checks, multifactor authentication (MFA), and more. Finally, PowerMax and PowerStore are being fitted with additional security capabilities such as enabling Trusted Platform Module (TPM) by default and locking data-in-flight/data-at-rest encryption. And of course, external key management systems are supported.
In addition to hardware-based capabilities on servers and storage systems, specific measures are also available in other areas such as networking, hyperconverged infrastructure, data protection, and management.
Networking
From a networking standpoint, Dell products protect customers’ networks with multiple rules and best practice configurations. Each security layer implements policies and controls, including network segmentation, centralized management, automation, and scalability.
Hyperconverged Infrastructure
Dell-based HCI environments inherit the security capabilities of Dell PowerEdge servers and benefit from rigorous supply chain integrity checks. The solution is architected upon the SDL principles, enabling an agile infrastructure with full stack integrity and comprehensive lifecycle management.
Data Protection
An essential component of any modern infrastructure, data protection acts as a line of defense to secure data across core, edge, and multicloud environments. Dell Data Protection simplifies and automates data protection operations at scale with accelerated data recovery and protection against ransomware attacks with isolation and vaulting solutions and services.
Management
A holistic security posture requires centralized and intelligent management capabilities with proactive and timely alerting to effectively thwart threats. The Dell CloudIQ management platform complements silicon-based security with ML-based predictive analytics to deliver real-time insights across the entire infrastructure stack.
Conclusion
In a data-driven world where sophisticated security threats are becoming the norm, organizations must take radical steps to protect their data and infrastructure while continuing to deliver against stringent business objectives. For IT infrastructure teams, providing stable, secure, and performant services is paramount.
Organizations must seek seamless integration of security capabilities and security validation processes (including secure supply chain validation) into their infrastructure without the burden of manual validation.
Dell Technologies provides a unique approach through the Dell Trusted Infrastructure framework. This holistic, zero trust IT security approach encompasses the entire Dell Technologies portfolio and provides secure supply chain provenance, silicon-based security, secure software development lifecycle, and enterprise-grade management capabilities.
Dell Trusted Infrastructure allows organizations to protect data and systems, enhance cyber resiliency, and overcome security complexity through a modern, resilient, and intelligent zero trust approach.