A feeling of impending doom looms as cybercriminal gangs take companies out one by one in the wake of AI explosion. Ultra-sophisticated threats have begun to emerge propelling their nefarious schemes forward.
At the Security Field Day event in California, the attending panel of delegates saw a solution in action that thwarts attempts of attack with the highest degree of confidence.
The Problem with One-and-Done Solutions
CISOs are responding to the growing cyber risks by allocating bigger budgets to tools meant to contain the damage. But as ransomware and malicious attacks become everyday menaces, increasingly businesses need a technology that can protect the perimeter as well as it can protect itself.
Often a one-and-done solution quietly turns vulnerable to manipulation and abuse by bad actors. Index Engines’ CyberSense puts an end to that risk. Jim McGann, Vice President of Strategic Partnerships at Index Engines, showcased this groundbreaking technology that can discover malicious code in the stack with 99.5% accuracy.
Signature Scanning Is Not Adequate
The biggest cyberattacks in the history all started with an oversight. Cybercriminals slipped in rogue software in the data. The intended purpose of the program was to evade detection and bide time. Like a ticking timebomb, this virus made the most impact when enough time had passed.
The common methods of discovery rely on signature-based detection, a technique that has proven effective only 50% of the time. Signature scanning involves looking for malicious footprints matching against a predefined repository of signatures known to the tool. But with threats reaching an overwhelming volume, it proves ineffective in spotting the newest and the sneakiest strains.
“Realize that folks that are bad actors have a bag of tricks. They have this whole shelf of stuff that they can use, and with the help of GenAI, they can modify and create new ones,” McGann says.
The stealthiest, most clever threats to exist today – the AlphaLocker, a new ransomware family, and WhiteRose, a ransomware-type virus that can evade detection owing to its ability to perfectly camouflage, are examples of this.
These programs execute corruption in a slow and methodical order that light-weight analysis tools and techniques fail to catch.
A category above this are the ultra-sophisticated variants like Xorist, Chaos and LockFile. These don’t leave behind fingerprints the way most viruses do, and are hence, devilishly harder to spot. “They represent about 60% of the variants that are being used,” he informs.
CyberSense for Maximum Detection Accuracy
CyberSense provides in-depth defense against small breaches to shockingly large ones. Notable for its ML-based detection and depth of inspection, CyberSense analyses and detects corruption hiding deep within the data. It can sense atomic malicious changes as easily as the conspicuous ones that operatives can never spot.
“We can’t do manually what CyberSense does,” says McGann. “It needs automation, intelligence. It processes millions of data points.”
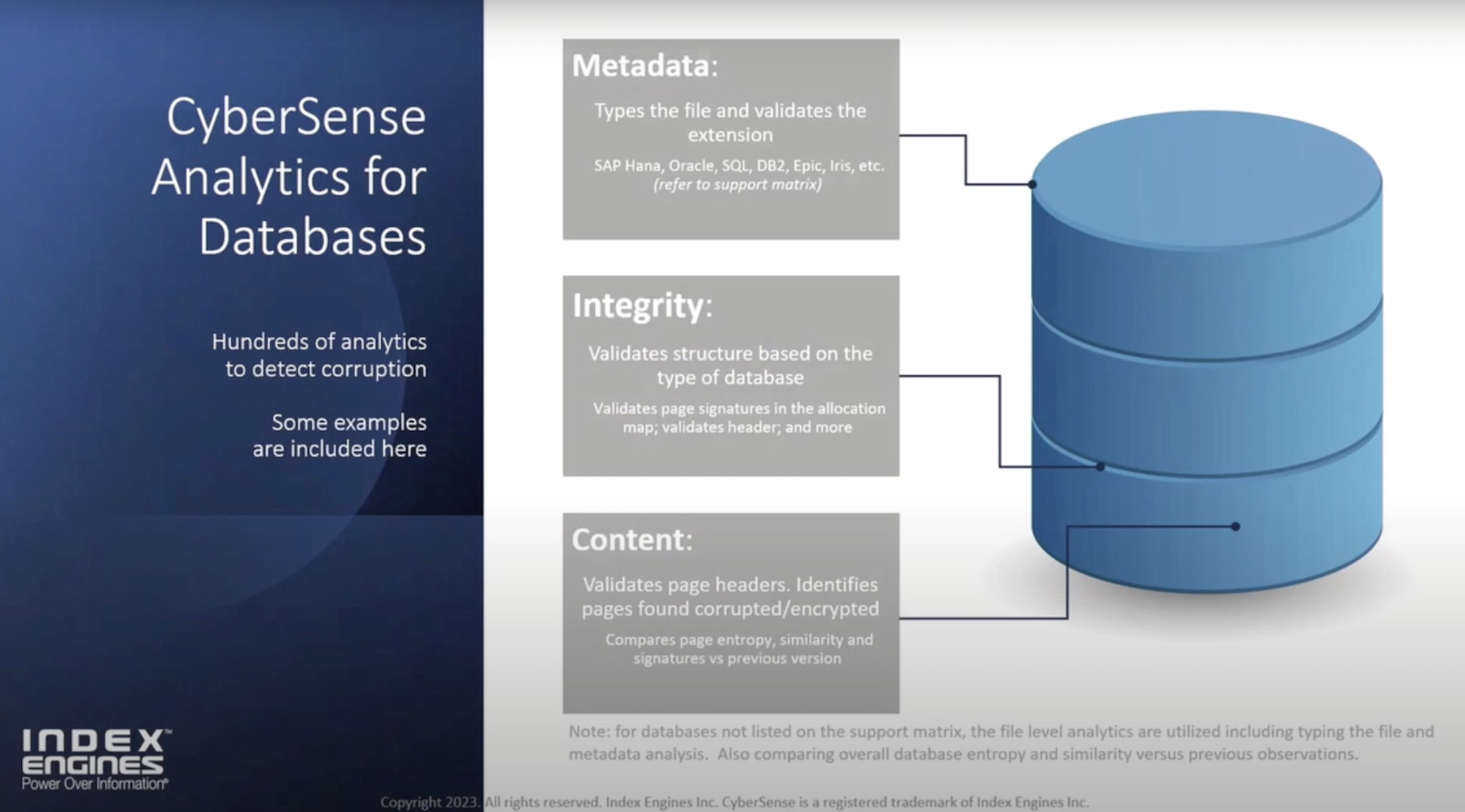
A misinformation companies are told often is that databases don’t get attacked. The reasoning being, corrupted databases cannot run and administrators will know at once that they are under attack. That’s not remotely accurate, says McGann. Databases too can be the hiding ground for suspicious objects that let it run as usual without giving away signs of attack.
CyberSense performs deep inspection of everything, starting with databases to the core infrastructure. It observes data, snapshots and backups, over time, to spot signs of corruption like encryption, mass deletion and suspicious changes.
“CyberSense is looking for corruption, not necessarily ransomware.”
For razor-sharp detection, CyberSense relies on machine learning. Its defining characteristic is broad training data and continual upgrades. Internally, Index Engines uses online subscription services like VirusTotal that analyzes suspicious files to diagnose the type of virus. This is topped with global research studies and anonymized customer data.
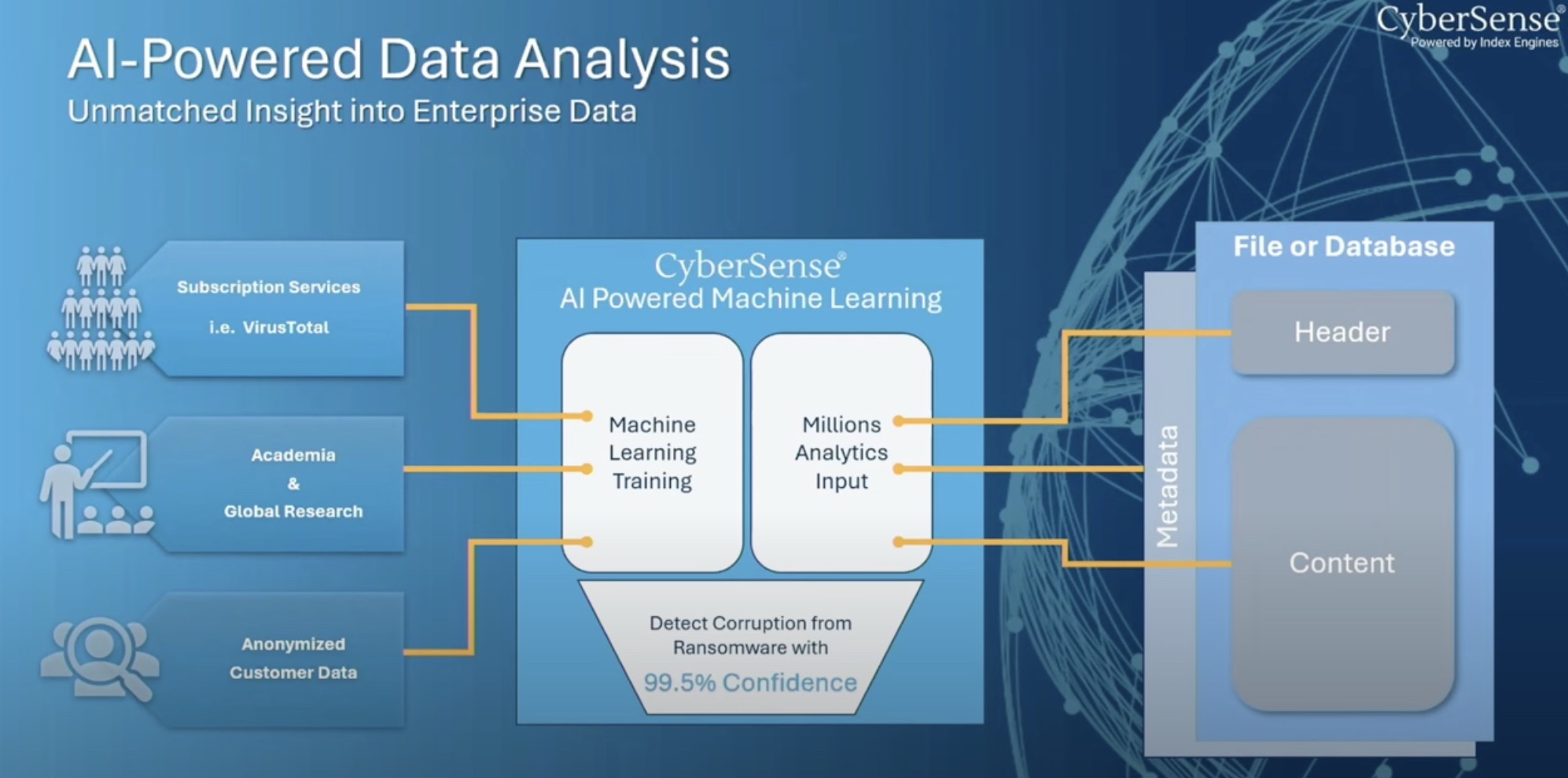
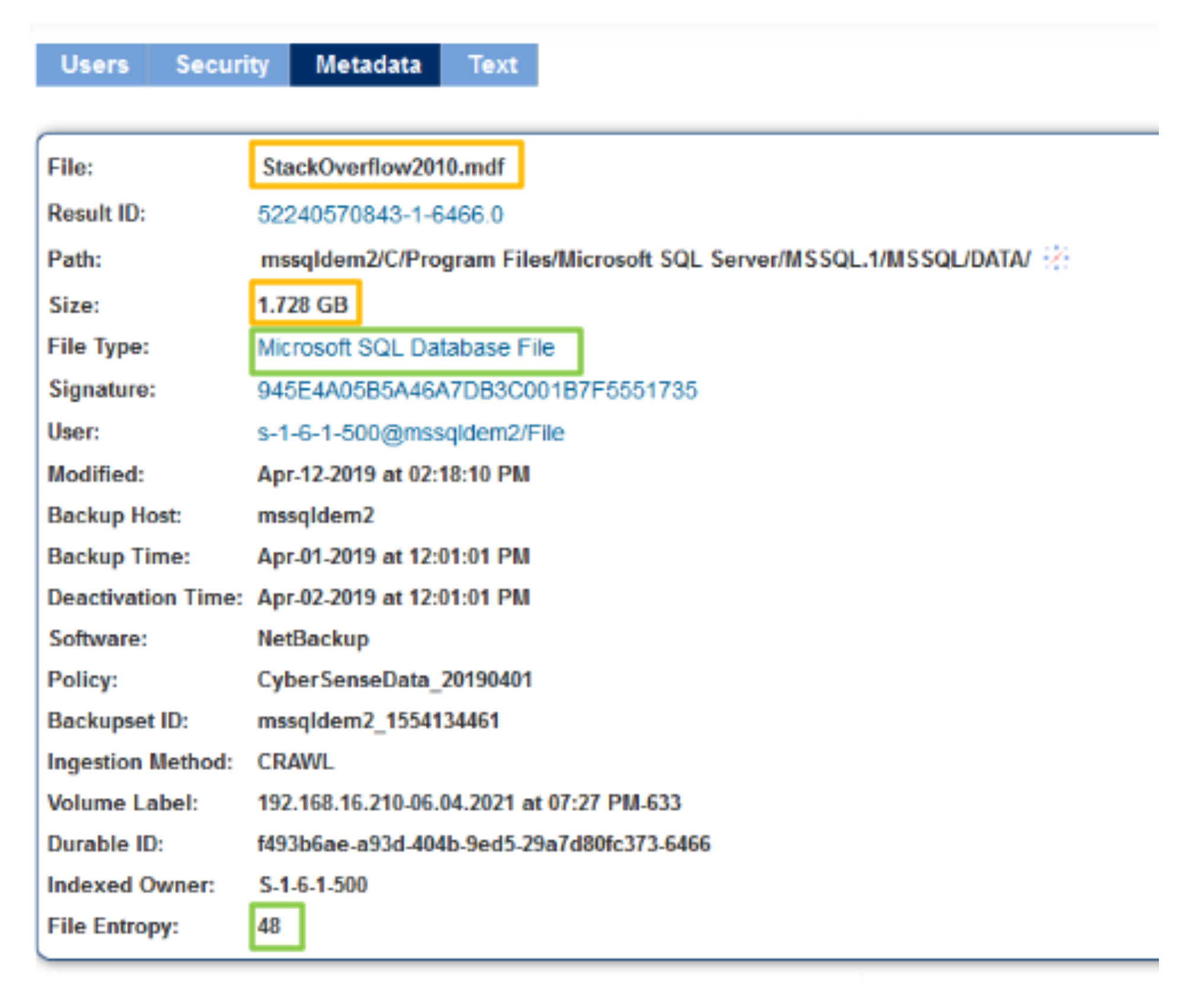
On the customer side, it scans files and databases in depth, meticulously inspecting all elements – the header, content and metadata. This produces millions of datapoints that provides fuel for the CyberSense AI engine to turn to insights.
Inside the CyberSense Lab where all the processing and analysis happens at the backend, ransomware behaviors are studied and classified into 5 categories based on their core behaviors. Latest ransomware variants are picked up from Index Engines’ dirty network and user data.
CyberSense Analysis is applied to this data. The ML operating behind the scenes runs through over 200 content-based analytics, and performs pattern recognition pushing out analytics.
“With CyberSense, when you scan data, every file, whether it be a PDF or Word document or the actual ransomware, gets a signature assigned to it so that when you’re in the recovery process, you could upload signatures into the CyberSense index and it’ll tell you if any of those signatures exist in the backups.”
As CyberSense detects a corruption, alerts bubble up on the dashboard with a complete post-attack forensics report attached showing details about the attack scale and blast radius. To accelerate recovery, the report also contains a listing of the last-known good backup to initiate recovery to.
For more, be sure to watch Index Engines’ presentation on this from the recent Security Field Day event. Krista Macomber’s report provides insights on the market trends and detection capabilities around ransomware that can be read on The Futurum Group website.