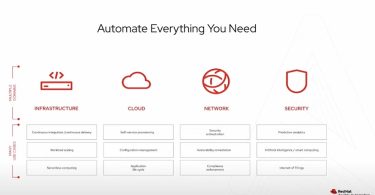
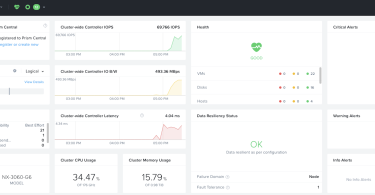
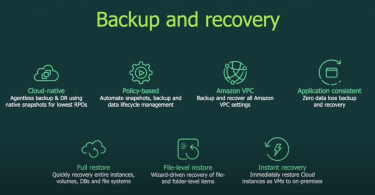
In this Cloud Field Day article, Sulagna Saha dives into Red Hat's presentation of the Red Hat...
Latest Articles
Disaster Recovery is a Security Function | Tomversations:...
In this episode of Tomversations, we look at disaster recovery and how it has been rebranded in the...
PCI Express 6.0 Finalized | Gestalt IT Rundown: January 19, 2022
The PCI Special Interest Group (SIG) announced last week that they have finalized the specification...
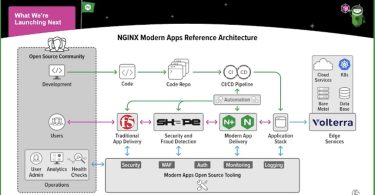
Application Modernization with Less Stress
In this post presented by NGINX, Chris Grundemann gives some highlights from his whitepaper to get...
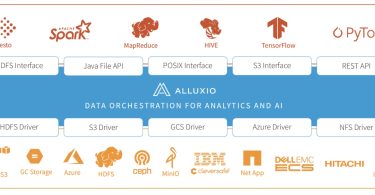
Alluxio: Bringing Ease to Access, Management and Orchestration...
In this exclusive article, Sulagna Saha talked with Jan Liband and Adit Madan of Alluxio about the...
Juniper Networks’ Mist Cloud Platform Just Got Better with Added...
In this Networking Field Day article, Sulagna Saha discusses Juniper Networks presentation for...
Amazon Enters 5G with AWS Private 5G
In this article, Kurt Marko talks in greater detail about 5G and Amazon’s new offering of 5G in his...
Why the Heck Even Use Deep Learning? | Utilizing AI 3×17
In this episode of the Utilizing AI podcast, Rich Harang joins Chris Grundemann and Stephen Foskett...
TAC Tales – Saving Configuration is for Quitters
A problem can be solved in a number of ways. But what happens when you have to dig deep to get to...
Hybrid Multi-Cloud Computing Made Simpler with Nutanix
In this exclusive article, Sulagna Saha spoke with SVP of Marketing at Nutanix, Monica Kumar, about...
Moxie Marlinspike Spins a Web3 | Gestalt IT Rundown: January 12...
Someone who has done a lot of thinking about what Web3 represents is Moxie Marlinspike. In a recent...
Achieving All-Round Data Protection at Minimal Cost with Veeam...
In this Cloud Field Day article, Sulagna Saha discusses Veeam Software presentation where they...