Threat hunting is more than just idle daydreaming. It's a process and a necessity to find exploits...
Latest Articles
Testing Phone-Sized Faraday Bags
In this post, Matt Blaze offers his expert on opinion on Faraday bags and which ones give you the...
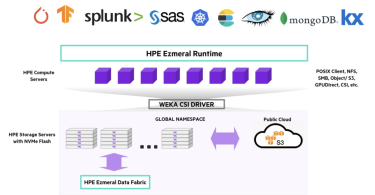
Weka Makes Significant Enhancements to SDS Performance and...
In this exclusive post, Sulagna Saha discusses WekaIO's flexible new storage solution and how it...
FlashArray//XL: Uncompromising Performance at Scale for Mission...
In this post presented by Pure Storage, Max Mortillaro discusses how the recently announced...
Intel in the Driver’s Seat with MobilEye | Gestalt IT...
Intel acquired Mobileye, the autonomous driving solution company, back in 2017 . They announced...
Security Effectiveness Reaches New Heights with Juniper Security...
In this post from October's Security Field Day Event, Sulagna Saha discusses Juniper Networks'...
The Easy Button for AI Performance
In this post presented by Intel, Chris Grundemann discusses why Intel's Python toolkit is changing...
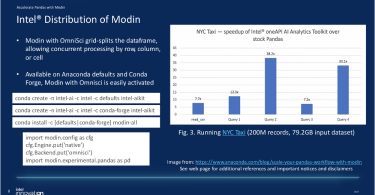
AI – Accelerated Performance at Scale with Intel and Python
In this post presented by Intel, Frederic Van Haren discusses Intel has invested significantly in...
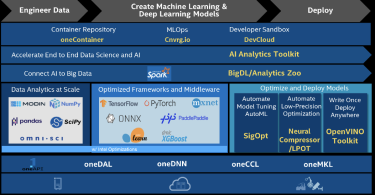
Intel – Python Data Science and Machine Learning at Scale
This Tech Field Day Showcase is sponsored by Intel and presented by Todd Tomashek, who discusses...
A Service Provider Network is Not Your Enterprise Network
Join Tom Hollingsworth on this episode as he brings on a panel of service provider networking...
The Fraud Supply Chain
Credit card scams are easy to detect, right? How many people could be involved in a crime like that...
Get Ready for Networking Field Day: Service Provider!
The inaugural Networking Field Day: Service Provider has finally arrived. Read on to learn more...