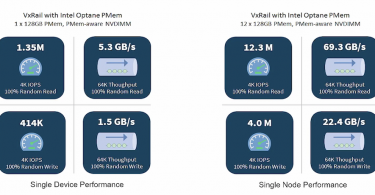
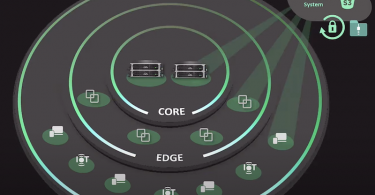
With virtual machines (VMs) at the forefront of many IT departments' task lists due to IT...
Latest Articles
Application-Centric Security
Applications are the basic building blocks of work today. How can you ensure they are secure for...
CTERA: Multi-cloud Unstructured Data Management
There's so much data at play in the modern enterprise, and storing it in an effective manner that...
Sensitive Data in Healthcare Needs Better Encryption
Many companies, especially in healthcare, need to store sensitive data. Encrypting that data not...
Juniper Breach Related to Encryption Flaw Reveals More | Gestalt...
Swiss-based firm, ProtonMail, is under bombardment for strict privacy questions. After five years...
F5 Doubles Down on NGINX Community with Sprint 2.0
In this interview, brought to you by NGINX, Calvin Hendryx-Parker had the opportunity to sit with...
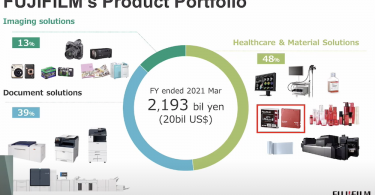
Handling Object Storage at Scale with Fujifilm Object Archive
Today's IT organizations need ways to handle data archiving at the massive scale of modern data...
Tech Field Day at NGINX Sprint 2.0: A Look Back on the Event
We were thrilled to be involved in NGINX Sprint for the second year in a row! Join us as we look...
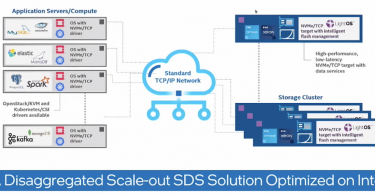
Intel and Lightbits Labs Make Storage Optimization Easy
Storage disaggregation allows IT professionals to make the most of their server architecture, even...
Service Mesh Is a Use in Search of a Problem
In this episode, Calvin Hendryx-Parker, Ned Bellavance, and Jason Benedicic join Stephen Foskett to...
Is Data Privacy Possible Anymore?
In this rapidly decentralizing, digitized world, is it even possible for us to maintain privacy...
Linux tc for SD-WAN Testing
If you need to test a new SD-WAN deployment and you don't have the resources to do it with a pre...