Whilst looking at the role that backups play in effective response plans to ransomware infection, we discussed in part one the value of identifying critical data, organizational knowledge to prioritize, and implementing an effective backup frequency. In part two, we are looking at the speed of recovery.
As you know from part one, ransomware can come into our systems in a variety of ways. Unless we put in controls to restrict this, our systems will not identify anything as wrong. Consider the number of phishing emails that organizations receive. One such phishing email might contain a malicious link or an infected document that contains ransomware. It could be navigating a user to a malicious website that requests to install an update but is actually malicious code. Or, due to  password reuse, a previous data breach provides a malicious actor with legitimate credentials, and these stolen credentials are then used to log in to a remote system. After the malicious actor is done helping themselves to whatever interesting files they may wish to take, they install ransomware to cover their initial breach.
password reuse, a previous data breach provides a malicious actor with legitimate credentials, and these stolen credentials are then used to log in to a remote system. After the malicious actor is done helping themselves to whatever interesting files they may wish to take, they install ransomware to cover their initial breach.
Consider each way you access and use systems or devices daily – these ways can all be used maliciously unless protections and limitations are in place. Ultimately, to protect systems and devices from ransomware (1) we need to configure our systems before infection to prohibit or limit this malicious code, and (2) once infected, only the prior controls and solutions in place can assist us in recovery – outside of making payment. Which means…
Backups are Sexy Even to Ransomware
Reading thus far, you might be thinking, “Wait we already have a backup and recovery plan.” Maybe restoration speeds and frequency of backups were considered when implementing – and it’s likely out of all of the organizations out there, some of them have considered this. However, remember, backups are attractive to more than just disaster recover/business continuity planners, historically take the authors of:
- SamSam: which gained access through remote desktop protocol (RDP), exploited other vulnerabilities identified to gain further network access, deleted backup files, and then started encrypting files.
- WannaCry, Locky, and Cryptolocker: which searched for and deleted Microsoft built-in Windows Volume Shadow Copy, often used by home users and/or SMEs.
More recently:
- DoppelPaymer: initially compromising a target through things such as Phishing or insecure remote desktop services, then traversed the network to identify privileged user accounts. Specifically, they were looking for domain administrative credentials to gain administrative access to cloud backup deployments and to delete an organization’s final option for non-payment recovery.
How can organizations protect themselves? For one, proper configuration of backups is a must, along with the principle of least privilege, i.e. all access required to do a job but absolutely no more. What about the backups themselves, can they limit what DoppelPaymer authors did?
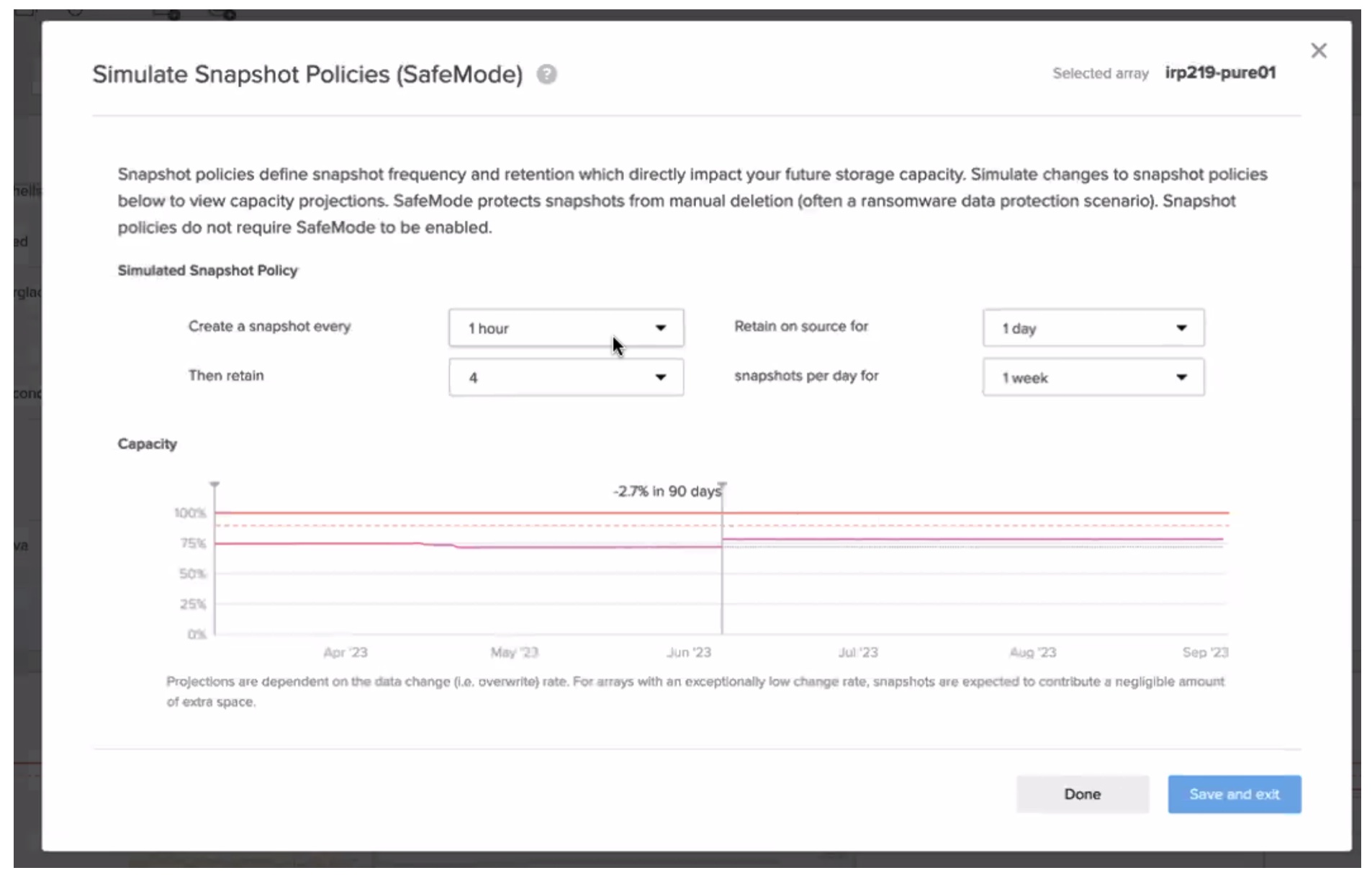
You may have read about immutable backups, i.e. configured to protect against change or deletion, but what if the domain administrator account is used? FlashBlade has something called SafeMode snapshots to address this. Where DoppelPaymer used administrative credentials to delete the backup, SafeMode snapshots do not allow for deletion. Protecting both the data within the backup and its metadata.
This is achieved through trusted contact(s) being authorized to work with Pure Storage support and restoring after an incident. Consider SafeMode as a last resort, whilst no additional fees are required, it’s when all layered-on controls have failed, the ransomware has infected the environment, and the malicious actor(s) destroyed or encrypted other backups. Still, the ransom does not need to be paid by the organization, as SafeMode backups require both the trusted contacts and PureStorage’s support working together to restore.
Historically, the advice from reputable sources has been inconsistent – some may pay, while others never pay. Where does your organization stand? Whilst participating within a “hat to hat” debate during The Many Hats Club IsolationCon a few weeks back, I shared my thoughts on why I believe ‘never pay’ is simply unfair. At times, it may cost too much to restore when not done properly – looking at the NHS example for lives impacted in article 1, but also the livelihoods of employees where an organization shut down due to the impact of an incident. This means that the best defense against ransomware is preparation, aligned to the realistic needs of the organization. The ultimate goal is to never pay, and fail-safes such as the option to enable SafeMode on backups enhances our never pay goal. Organizations that implement fail-safes, addressing the ‘worst-case scenario’ preparation are still succeeding in disaster because they are not left in a position where the only choice left is none.