In this article, Sulagna Saha brings to light Brian Greenberg's top five cybersecurity issues of...
Latest Articles
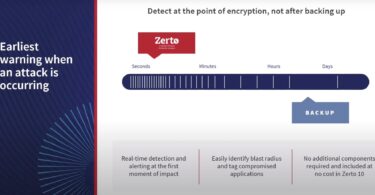
Preventing Attack Escalation with Real-Time Encryption Detection...
In this Cloud Field Day article, Sulagna Saha discusses how Zerto's Zerto 10 strikes at the heart...
Getting Off the Storage Refresh Treadmill with StorPool
In this Storage Field Day Tech Note presented by StorPool, Jim Czuprynski discusses how radically...
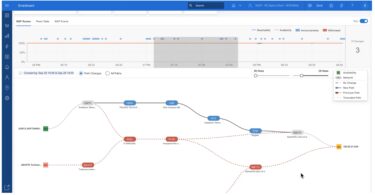
Catchpoint BGP Monitoring
In this Networking Field Day Tech Note presented by Catchpoint, Peter Welcher discusses how...
Pure Storage Takes Aim at Disk Storage | Gestalt IT Rundown:...
We're at Pure Storage's Pure Accelerate conference this week, and the buzz is focused on the...
Building Better Applications at Reduced Cost with Couchbase
In this Cloud Field Day article, Sulagna Saha discusses how Capella from Couchbase and how the...
Understanding the Hype around Generative AI
In this article, Sulagna Saha highlights Jody Gajic's thoughts on the generative AI wave and the...
Machine Learning is Best Suited for Security
Although artificial intelligence, specifically machine learning and large language models, is in...
Integrating Native Data Protection into Any Infrastructure...
In this Cloud Field Day article, Sulagna Saha discusses how enterprises have been dreaming of a...
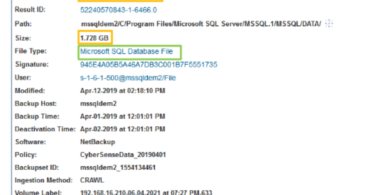
Ransomware is a Real Threat but CyberSense From Index Engines...
In this Tech Field Day article, Denny Cherry discusses how any company that is worried about...
Economics of Edge Computing with Carlo Daffara of NodeWeaver |...
When it comes to edge computing, money is not limitless. Joining us for this episode of Utilizing...
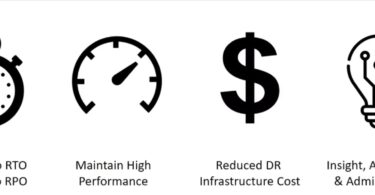
DR as a Service with JetStream Software
In this Cloud Field Day article, Sulagna Saha discusses how JetStream delivers extended protection...