If you’ve been following along with my recent posts in this series, you already know that the traditional enterprise WAN architecture is being disrupted by digital transformation initiatives, increasing cloud adoption, growing remote user populations, and a much-needed focus on enterprise security. You also know that SD-WAN is the network methodology needed to address these changes and the challenges they place on your legacy WAN design.
If you’ve been following along with my recent posts in this series, you already know that the traditional enterprise WAN architecture is being disrupted by digital transformation initiatives, increasing cloud adoption, growing remote user populations, and a much-needed focus on enterprise security. You also know that SD-WAN is the network methodology needed to address these changes and the challenges they place on your legacy WAN design.
However, now is not time to get comfortable. We’re all aware that in the world of IT the only constant is change, and WAN architecture is no exception. While we’ve all just started to wrap our heads around the idea of a Software-Defined Wide Area Network (SD-WAN), a new reality has emerged. The reality I’m referring to is the emerging requirement to combine networking and security in order to keep pace with the evolving requirements on today’s digital enterprise. I wrote about this specifically in a fairly recent post about NSX Cloud, titled “The Power of Combining Policy and Availability.”
While that post was all about securing workloads wherever they reside, the basic concept applies equally to the networks that tie our offices to our data centers, to our multiple clouds, to our remote users and devices. Gartner says that the solution to this trend is a secure access service edge or SASE, which is pronounced ‘sassy.’ So, as you might have guessed, in this post we’ll take a look at how VMware SD-WAN by VeloCloud can make your WAN “sassy” by providing exactly the platform you need to deploy your own SASE WAN.
A Secure and Mobile Workforce
Before we dive into specific SASE capabilities or architectures, let’s level set by taking a look at the why: Why do you need a SASE WAN?
As any good network or security architect knows, the technologies, methodologies, and architectures we design and deploy must never be the end in themselves. We don’t deploy a Clos architecture in our data center just because we heard it’s the new exciting thing to do. We don’t adopt a zero-trust architecture just to say we did. We leverage technology to meet business goals, to satisfy our organization’s unique requirements, objectives, and constraints (ROCs).
It turns out that the trends mentioned above (digital transformation, cloud adoption, remote users, security threats) create a set of challenges common to most modern enterprises. When your users are working on devices you don’t control, connecting over networks you don’t control, to cloud services that are also largely outside of your control, where and how do you insert the needed security?
Once upon a time, this was easy. When all of your users, servers, and data were inside a single office you could just lock the doors and place a firewall on the internet connection. Now that users, data, devices, and workloads are largely outside of the data center, and not even on the corporate network, things have changed. The new reality is one of de-perimeterization. The new goal is a secure and mobile workforce. And SASE can help us get there.
SASE (Secure Access Service Edge) Overview
What is SASE? Sure, it’s a secure access service edge. But what does that mean? According to Gartner (who coined the term), “SASE offerings will provide policy-based ‘software-defined’ secure access from an infinitely tailorable network fabric in which enterprise security professionals can precisely specify the level of performance, reliability, security, and cost of every network session based on identity and context.” So it’s a set of capabilities that enable us to combine policy and availability in the WAN.
What are those specific capabilities? Here are a few key pieces of the SASE puzzle:
- CASB – Cloud Access Security Broker
- SD-WAN – Software-Defined Wide Area Network
- SWG – Secure Web Gateway
- FWaaS – Firewall-as-a-Service
- ZTNA – Zero-Trust Network Access
Of course, there are other technologies that will eventually be tied into an advanced SASE architecture, such as:
- WAAP – Web Application and API Protection
- UEBA – User and Entity Behavior Analytics
- CDN – Content Distribution Network
- WAF – Web Application Firewall
- UEM – Unified Endpoint Management
The list can go on and on, additionally including remote browser isolation, recursive DNS, network sandbox, Wi-Fi hotspot protection, network obfuscation/dispersion, and offline edge computing protection, to name a few more.
But how does SASE apply these components to get us closer to our goal of a secure and mobile workforce?
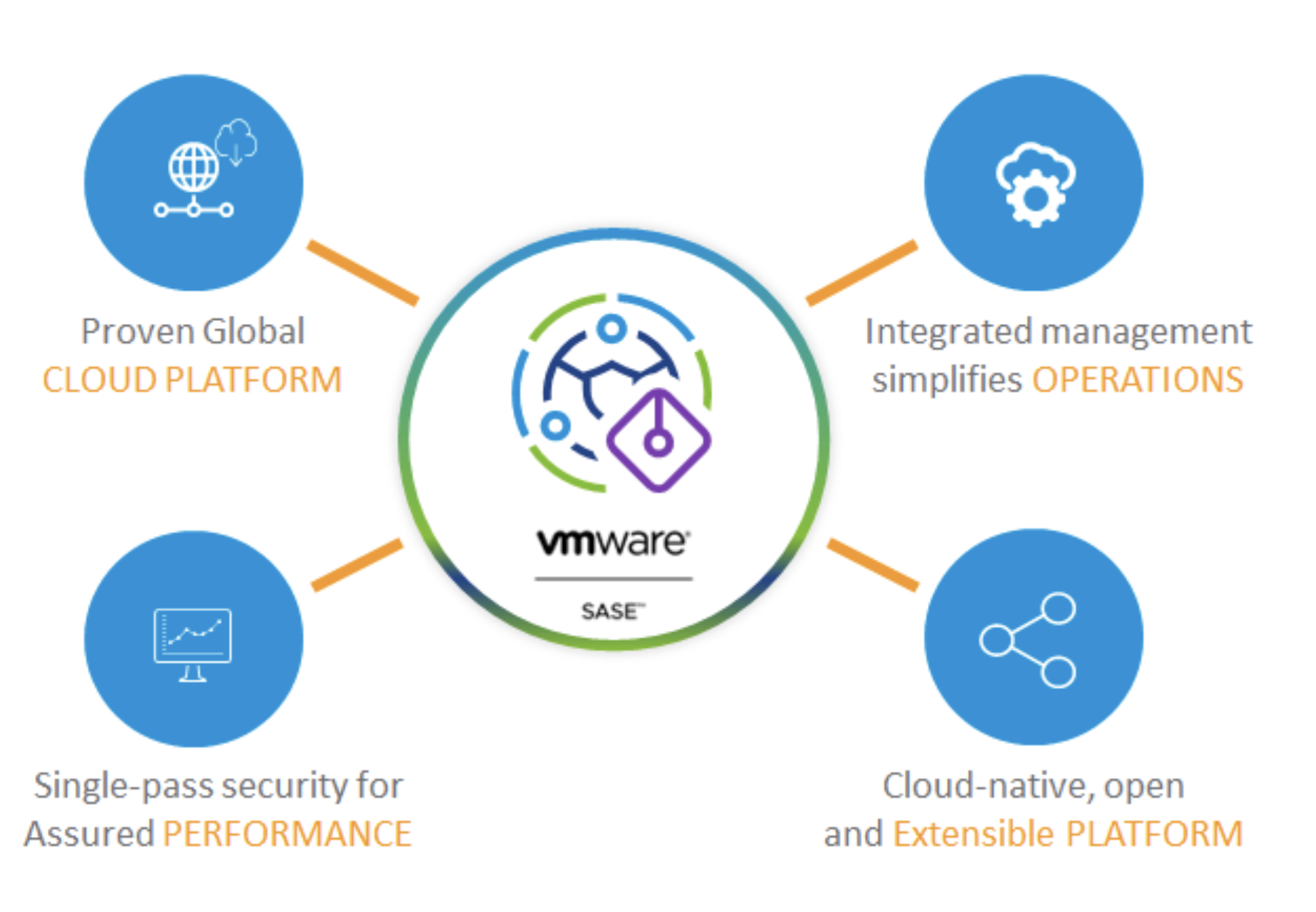
We never want technology for technology’s sake. Learning a bunch of acronyms may be fun, but what we really need is an architecture that improves network and security performance while making the whole thing easier to operate and scale. I would argue that there are five core characteristics of a SASE WAN, which provide the benefits we need:
- Converged network and security: We need to combine policy and availability in order to ensure secure communication in a distributed digital enterprise. Tear down those silos and shift security left.
- Identity-based: Forget about zones, VLANs, and IP addresses. What we want is a set of universally applicable network and security policies based on the identity of the communicating entity (user, device, workload, etc.), along with additional context whenever possible.
- Cloud-native: Get out of the box! In order to provide the flexibility, adaptability, and scalability needed to define and defend those enterprise-wide, identity-driven policies most efficiently we need to transcend physical devices or locations and leverage a cloud-native architecture that distributes inspection and enforcement.
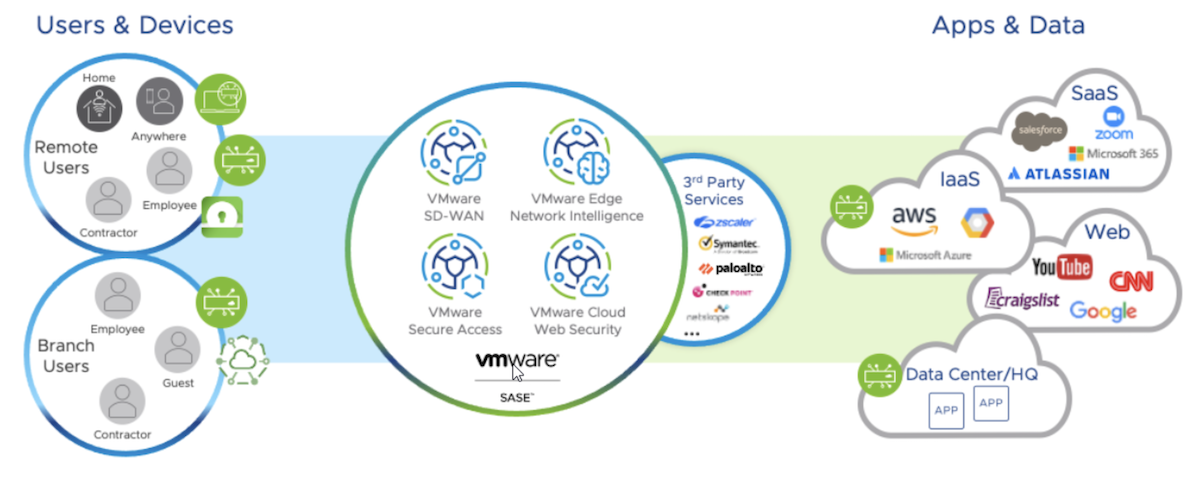
- All the edges: Just as we can no longer focus on providing secure connectivity for only those devices that happen to be on the corporate network, we cannot settle for a WAN that only connects some of our edges. We must support all the edges. This includes headquarters, data centers, branch offices, cloud resources, and mobile users – on both managed and unmanaged devices.
- Global reach: Latency matters. And who knows where business will take you, or your users and partners next? In order to provide the best possible experience, we need to ensure that we don’t fall back into that data-center-centric trap of tromboning traffic. Our converged network and security platform must be available everywhere we (might) operate.
Sounds great, take my money!
Not so fast. According to Gartner, it’s going to take something like five to ten years for SASE to reach the mainstream market. They peg current adoption at less than 1% today, mostly because the market is maturing and there aren’t many (if any) fully mature and comprehensive SASE providers yet.
Help Me, VeloCloud. You’re My Only Hope.
Chances are you got that Star Wars reference. And if you did, you know that Princess Leia Organa can be about as sassy as they come (almost as sassy as Han Solo, or even R2-D2, if you ask me). That’s obviously not a coincidence. Just as General Kenobi was able to help Leia save the universe, VMware SD-WAN by VeloCloud can help you save your WAN. And it can do that by making your WAN as SASE as you like.
Let’s take a look at how VeloCloud stacks up to the five core characteristics of a SASE WAN we identified above:
- Converged network and security: As you might remember from my previous post, the VMware SD-WAN Edges are literally built to provide secure connectivity, whether through built-in firewall features or automated, policy-based access to partners’ advanced security services. It’s not just the Edges though, VMware SD-WAN Cloud Gateways also include integrated networking and network security capabilities, making the convergence end to end across the entire “Network of Clouds.”
- Identity-based: VeloCloud has advanced application visibility capabilities, and the Cloud Gateways identify each end client, steering and optimizing application traffic through the Network of Cloud Services to deliver the best user experience, and the needed security services.
- Cloud-native: Those Cloud Gateways, the autonomous, stateless, horizontally scalable backbone of VMware’s Network of Clouds are, of course, cloud-delivered. And the Edges come as a hardware or virtual appliance, allowing direct-to-cloud deployment when needed.
- All the edges: As you may have guessed by now, this is another inherent feature of the VeloCloud architecture; the multi-service Network of Clouds meets users and applications wherever they are, be it campus, branch, data-center, cloud, or fully mobile.
- Global reach: VMware has deployed over 2,000 Cloud Gateways in over 200 major cloud, co-location, and connectivity provider PoPs around the world.
High marks across the board.
The story doesn’t end there though. Just as SASE is more than SD-WAN, VMware is more than SASE. VMware is making security intrinsic to everything they do for the modern distributed enterprise. This is laid out in a recent press release where they discuss:
- An Intrinsic Approach to Workload and Endpoint Security with Carbon Black
- Redefining Internal Data Center and Multi-Cloud Security with NSX
- VMware Intrinsic Security Addresses the Secure Access Services Edge with VeloCloud
- Proactive Management of Public Cloud Risk with VMware Secure State
- Simplifying Zero Trust Access to Any Application Across the Digital Workspace with Workspace ONE
The primary reason that VMware is the best choice to save us from legacy WAN failures with a SASE WAN is its products and features stretch so far beyond the WAN. I guess you could call that the secure access service enterprise – and that’s still sassy.